A Smarter Way to Work
Made for people who live in their calendars
ekai captures your meetings, surfaces key insights, and keeps everything organized by topic—so you can focus, take action, and avoid context switching.
Meeting Twin
Surfaces Insights & execute Follow ups.
Your Personalized knowledge base
Organizes Knowldge by Topics & generate on demand documents.
Handles repeated queries
Your team remians unblocked even when you are not available to respond.
What Can Your ekai Do?
Uninterrupted work, clear information
What Can Your ekai Do?
Uninterrupted work, clear information
Meeting Insights
Private & Contextual GPT
Available 24x7
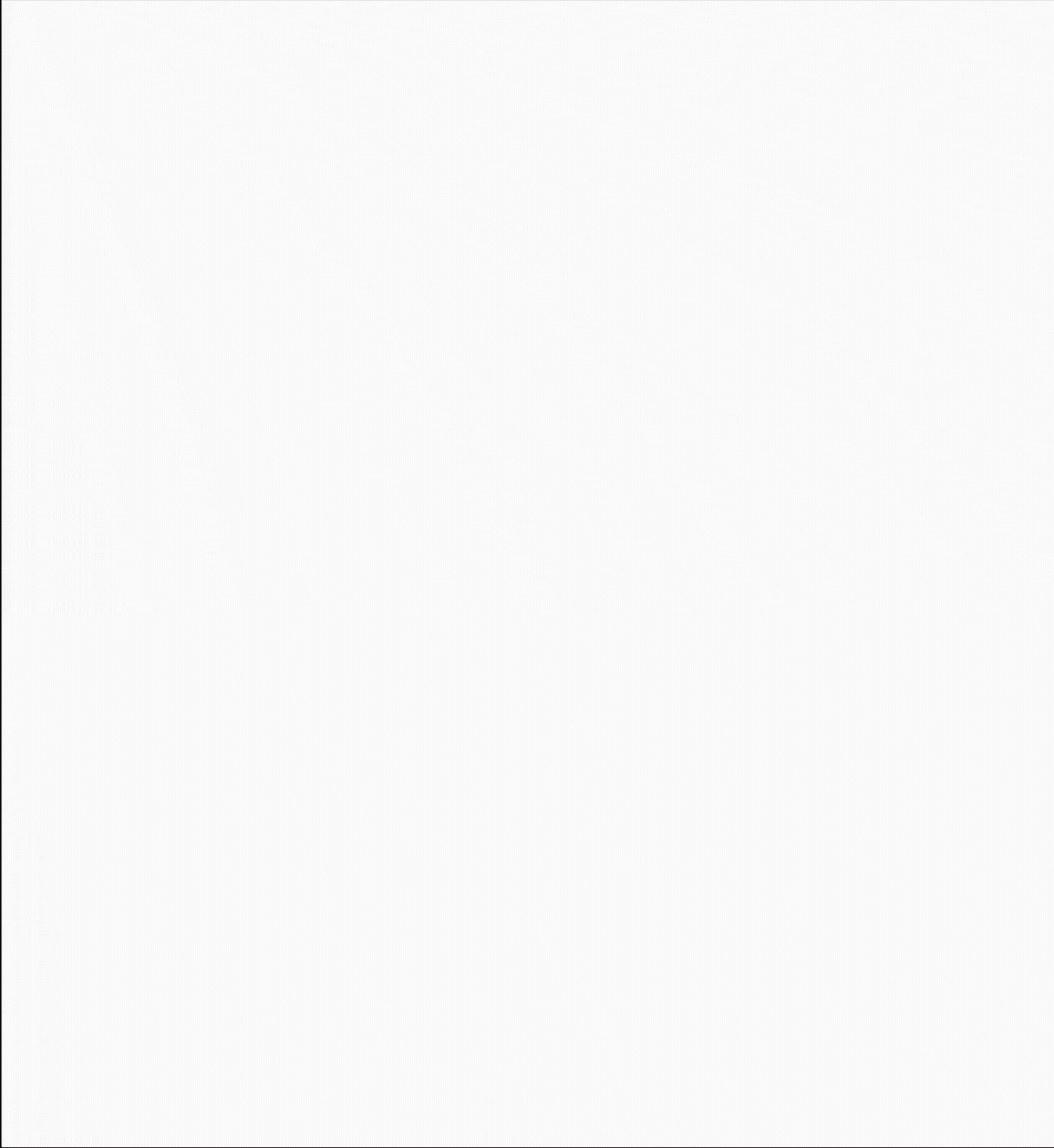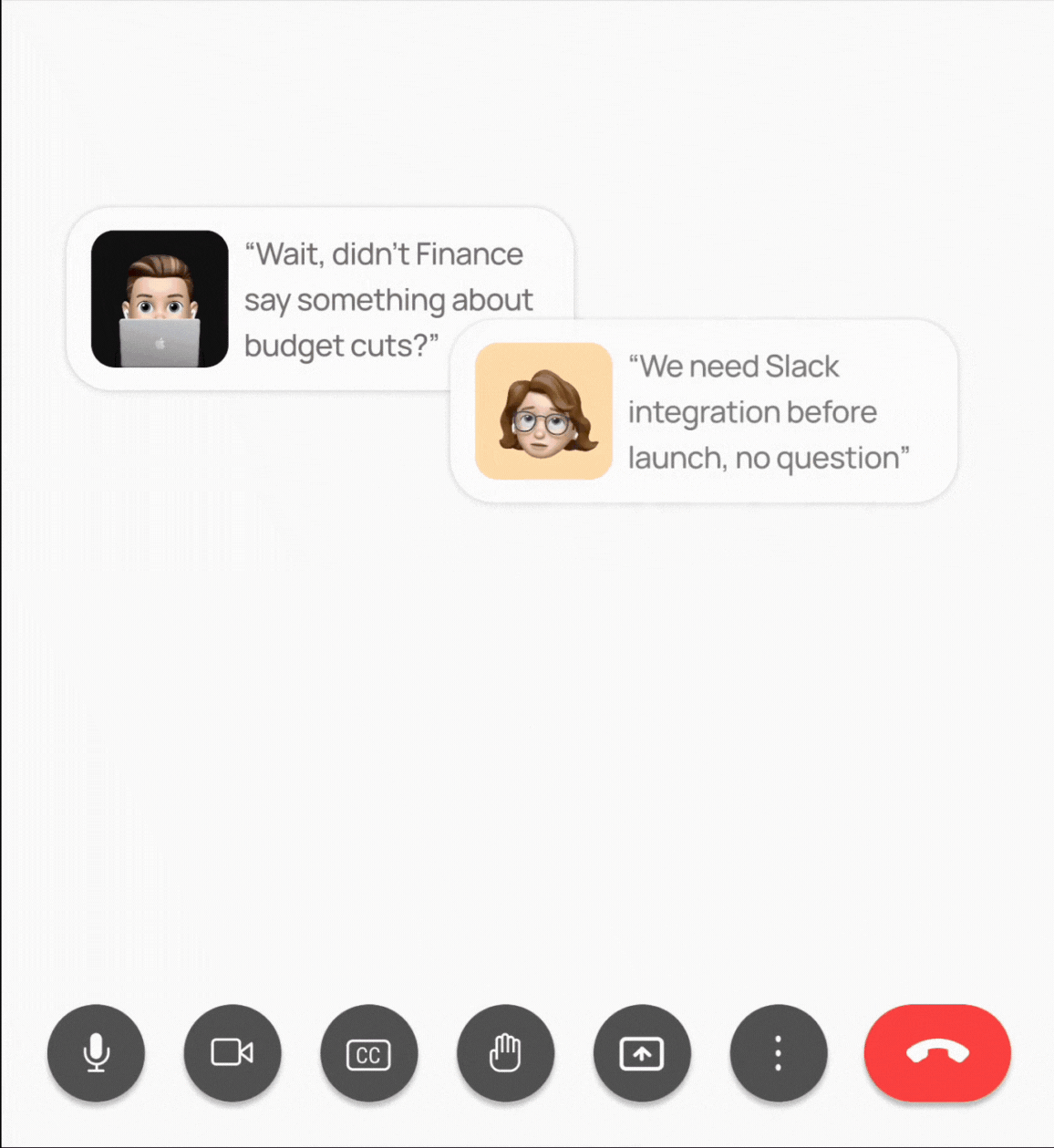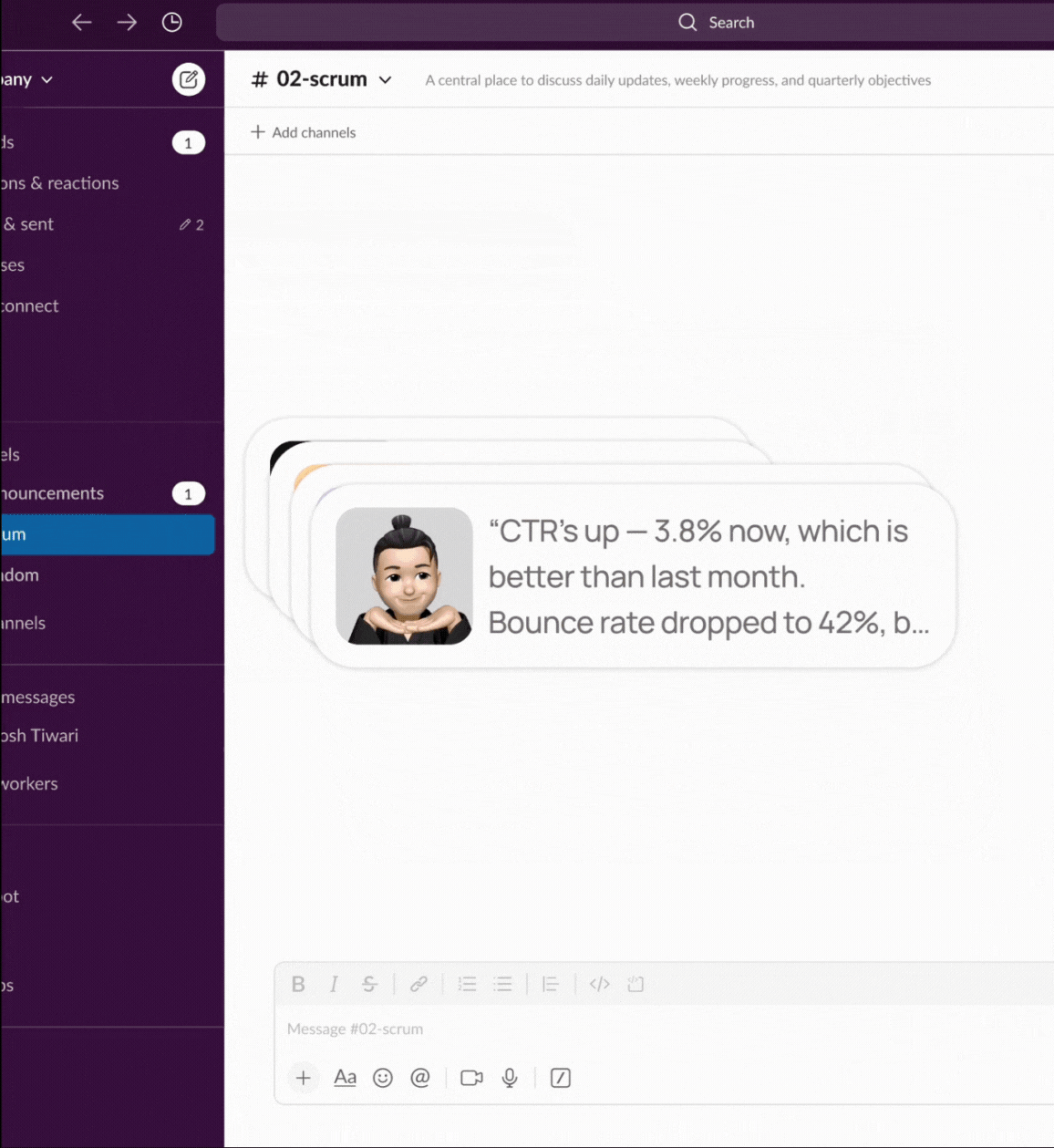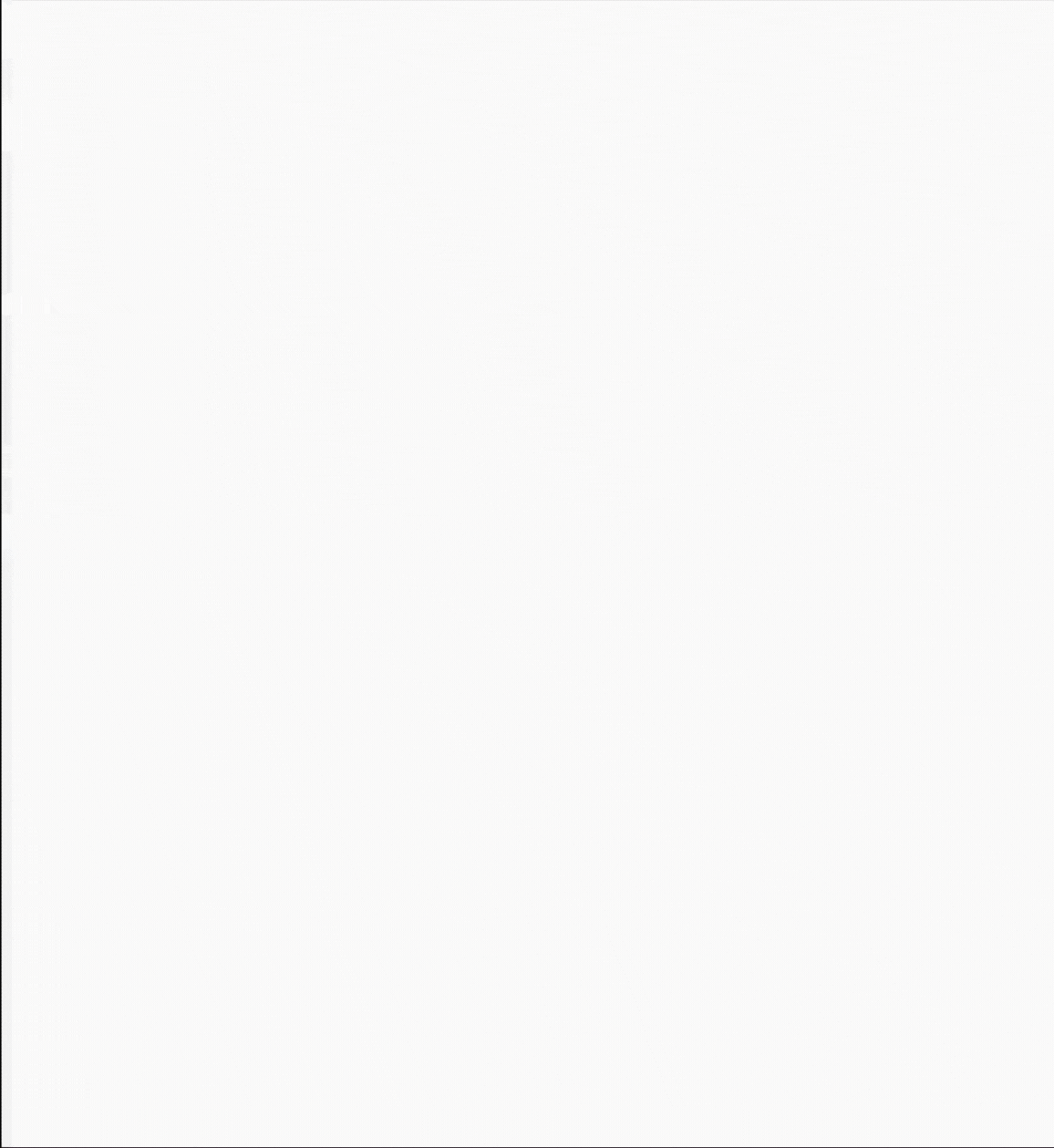
How ekai Works
Your AI Twin. Your Knowledge
Supercharged by AI.

Hi @Mike This week, we delivered the Slack integration setup and shared the first draft of their custom onboarding flow. We also resolved their calendar sync issue reported on Monday.
What Sets ekai Apart
Your AI Twin Trained by You,
For You, to Represent You
Make Meetings work for you
Not just summary, but moves work forward by automating your post meeting workflow.



In-House Private GPT
Gives you access to an in-house LLM within your workspace.
Your Private Cloud
On-premise Server
Your Personalized AI Twin
Gives you full control, remembers & takes action on what you need.


Available as Co-Pilot or Auto-Pilot.
Be in control with Co-pilot for important discussions and Auto-Pilot when you need time for yourself.
Your Data, Your Control
We implement enterprise-grade security to protect your valuable information
Data Encryption
Your data is safeguarded using TLS encryption during transmission and AES-256 encryption at rest. Our secure key management system includes regular rotation protocols to maintain the highest level of protection.
Access Control
We strictly enforce your existing permission structures, ensuring team members can only access information they're authorized to view. Your organization's security boundaries remain intact at all times.
Flexible Deployment
Deploy our solution on your own infrastructure for complete control over your data environment. Configure the implementation to align with your specific security policies and compliance requirements.
