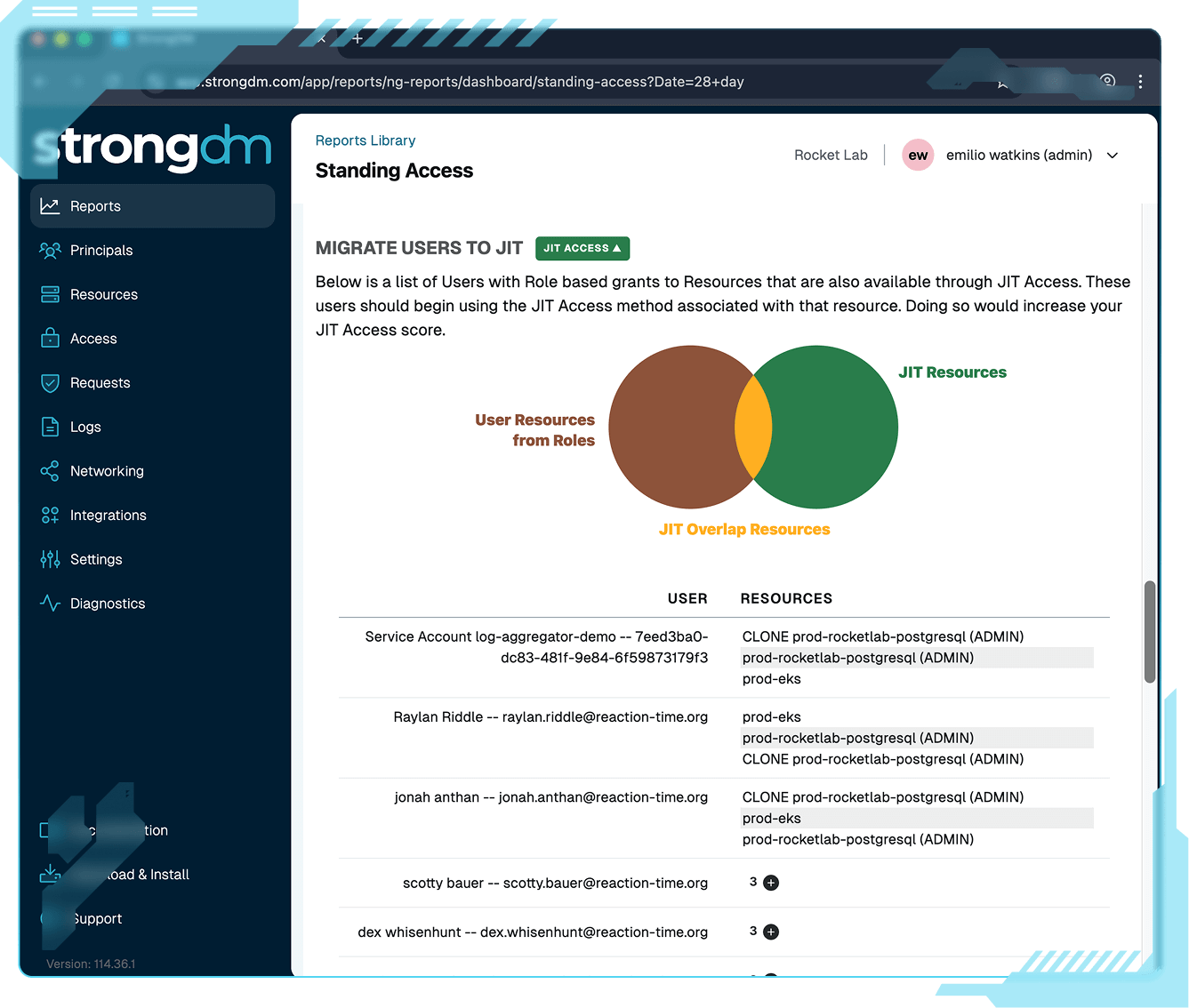
CONTROL WHAT HAPPENS AFTER LOGIN.
AUTHORIZATION AT RUNTIME. PRODUCTIVITY IN REAL TIME.
StrongDM gives you the control PAM promised but never delivered. Enforce policy in real time, eliminate passwords, and meet developers where they are.
Secure Access With
Universal Privileged Access & Authorization
StrongDM enforces policy and authorization continuously with adaptive action controls, full session visibility, and no standing privileges. Built on our Identity Firewall foundation.
Traditional access control stops the moment a session starts. After that, you're left with a static log, hoping it captures the full story across your ephemeral infrastructure. StrongDM replaces that gap with live, in-session control over every action and full visibility across your entire stack. It’s security you can prove, not just assume.
Transform Identity Security
Don’t rip and replace your security stack, augment and accelerate it. Protect your existing security investments while gaining cloud-native capabilities, reducing operational overhead, and achieving audit readiness in days, not months.
Eliminate Breach Risk in Real Time
Credential theft is the #1 attack vector. StrongDM eliminates it entirely, preventing lateral movement, reducing cyber insurance costs, and protecting your business without slowing down operations.
Secure Cloud and Hybrid Infrastructure
Your security stack shouldn't dictate your infrastructure choices. Move faster across AWS, Azure, GCP, and on-prem with unified security that deploys in minutes and scales automatically—enabling innovation, not blocking it.
Unleash Your Productivity
Your competitors move fast. StrongDM makes it so you don’t have to choose between security and productivity, accelerating release cycles while strengthening security posture. Turn compliance into a competitive advantage, not a constraint.
Your Zero Trust
Privileged Access Management Platform
Before StrongDM
After StrongDM
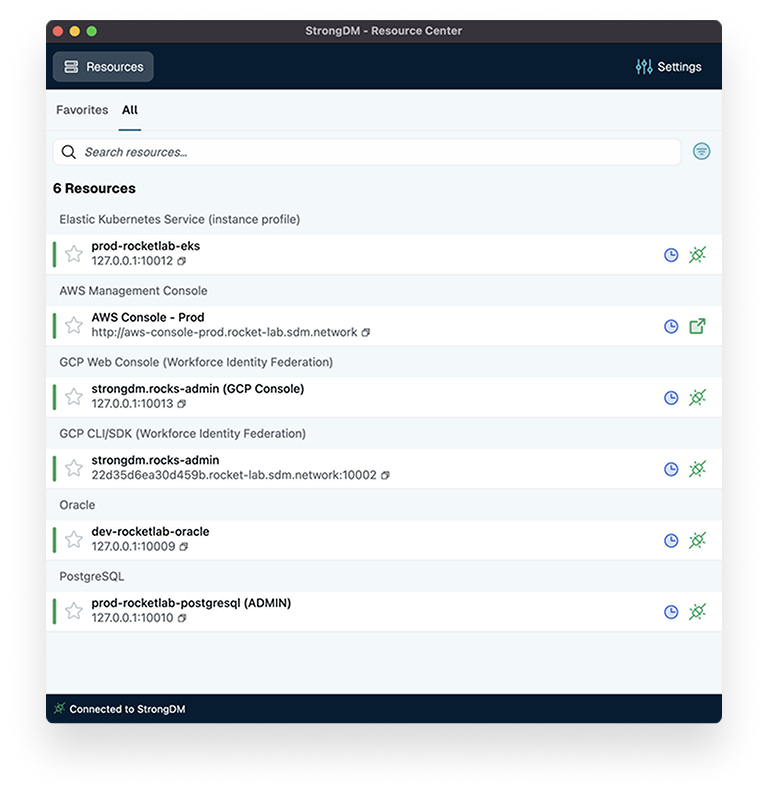
See the StrongDM Difference
Policy Engine
Centralized Policy, Unified Control
Centralized Policy, Unified Control
StrongDM’s Cedar-based Policy Engine continuously evaluates user, device, resource, and risk context to authorize access at runtime. Define once, enforce everywhere, and adapt instantly as conditions change across your cloud, hybrid, and on-prem environments.
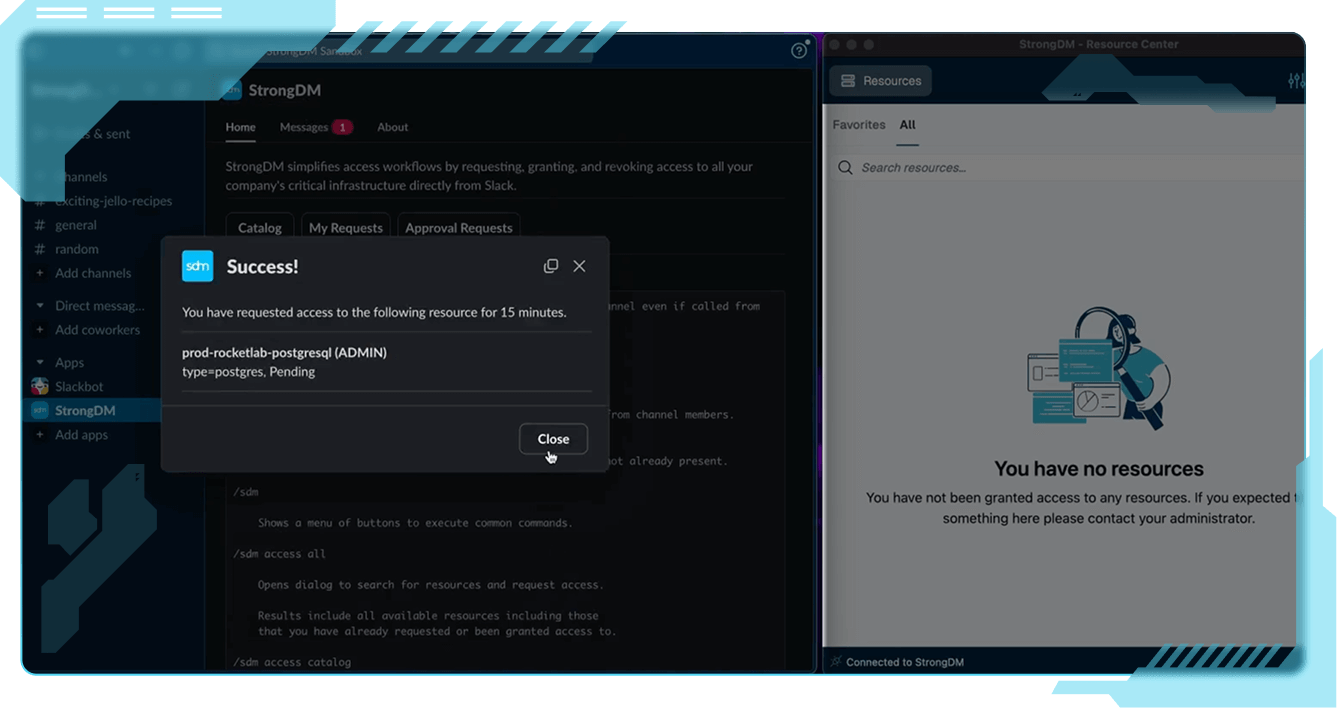
Security at the speed of your infrastructure
StrongDM enforces policy and access continuously, not just at login, to adapt in real time as conditions change. Every action, session, and identity is authorized at runtime for uncompromising control.
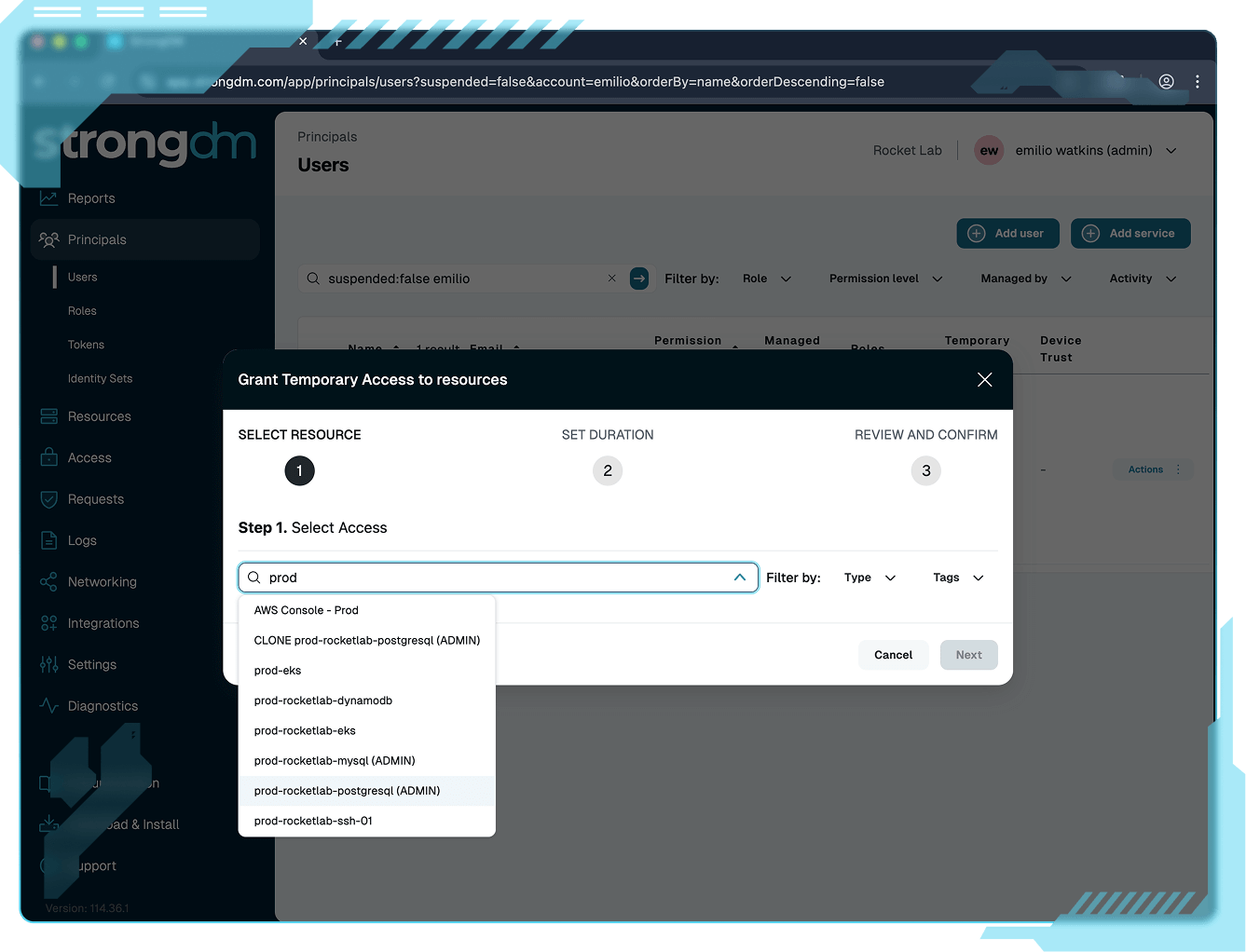
Security that doesn’t slow you down
Built for developers, operators, and security teams alike, StrongDM delivers Zero Trust control that integrates cleanly into existing workflows. No context switching, no waiting, no frustration.
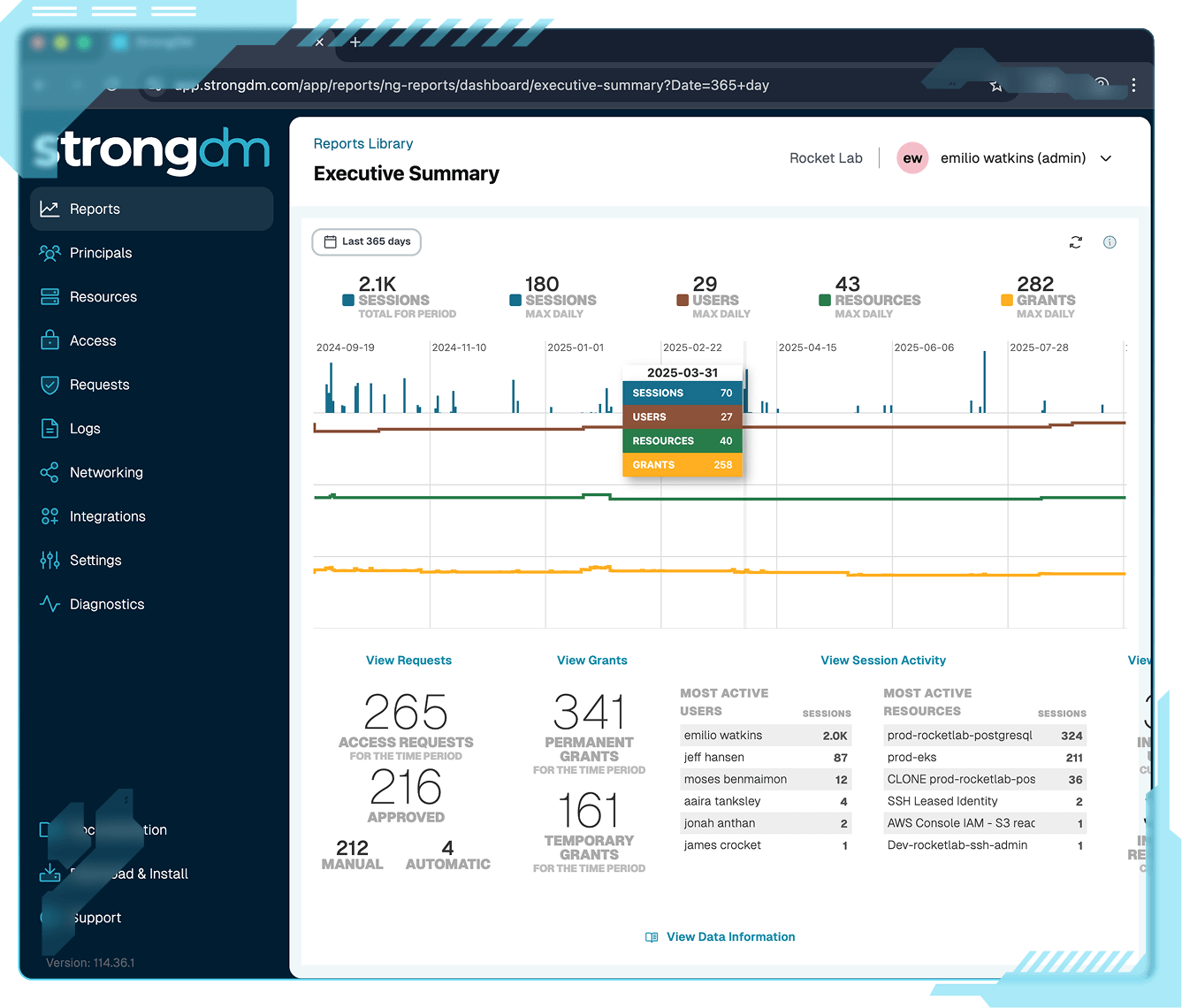
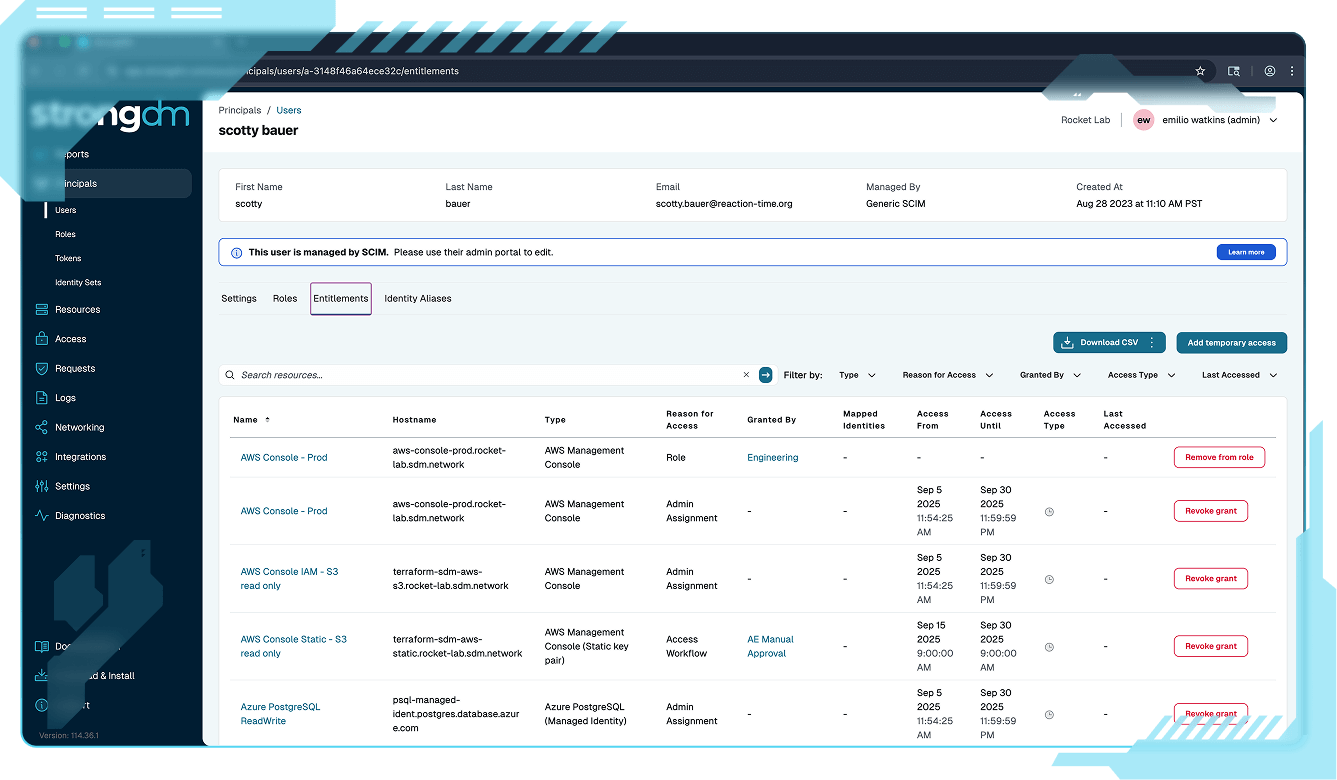
See everything, miss nothing
Capture and monitor every session across users, machines, and agents in one unified view. StrongDM eliminates blind spots and provides the audit-ready visibility legacy PAM can’t.
No code required
StrongDM layers on top of your existing stack with no migration or code changes. Deploy in hours, not months, and modernize your access model without breaking what works.
Backed by a world-class customer experience
“Security is a necessary part of day-to-day life. In terms of how we go forward, StrongDM will continue to be part of that story. It has all the mechanisms in place for database access control that we require, and I haven’t found a competitor yet that does the same thing.”
Wes Tanner VP Engineering, Zefr
“We chose StrongDM because the solution is the one solution to rule them all. You simply integrate all your data sources into StrongDM; you integrate all your servers into StrongDM; you integrate all your Kubernetes clusters into StrongDM. You give your developers one simple tool they need to connect using SSO, and they have access to what they own.”
Jean-Philippe Lachance Team Lead - R&D Security Defence, Coveo
“Clearcover remains committed to the industry’s best security practices. StrongDM provides us with better insights to bolster our security posture.”
Nicholas Hobart Senior Engineer, SRE Team, Clearcover
“I would urge all other CISOs to adopt strongDM as their database proxy platform. It's been amazing for all of our users. When we first got strongDM, we implemented within, I think a day. And within a week we saw more and more users requesting access to it, once they saw how easy it was to access databases.”
“With StrongDM, people don't have to maintain usernames and passwords for databases. With servers, they don't have to have keys. For websites, they don't have to have passwords. And so when you start eliminating the need for passwords and you start looking at things like Zero Trust, I believe that the attack surface is completely reduced.”
David Krutsko Staff Infrastructure Engineer, StackAdapt