Cameras Recorders Microphones Software Publications |
|
| |||||||||||||||||
|
Bugs Phones WikiLeaks ← IP-19
The bug circumvents the device's strong encryption, by connecting
directly to the audio circuits.
It is passive in that it does not transmit the
intercepted conversations immediately. Instead, it records the
conversations in its internal memory. Upon receiving a remote
command, it transmits the recorded conversations (probably
encrypted) in a short wideband burst. This makes it virtually
impossible to detect and discover the device in a regular
bug sweep.
➤ Location of the bug
It is difficult to determine the origin of this bug,
but given the fact that it is professionally made in quantity
and that it is tailor-made for this type of telephone, it seems
likely that it was a state actor, probably the US
Central Intelligence Agency (CIA).
Note that this covert implant is not only suitable for the
CryptoPhone IP-19, but for every Snom IP-phone
that uses the same chassis.
The diagram below shows how the system worked. At the left is the
Listening Post (LP) with a command transmitter and a receiver.
At the right is the modified CryptoPhone IP-19 of which
the keypad board is substituted by a replacement board of identical size,
that contains the implant.
The implant was placed inside an IP-19 CryptoPhone in such
a way that it was virtually invisible, even after opening the device.
To understand how and where it was located inside the telephone, we will
use the photograph of the interior of a regular
IP-19 CryptoPhone (below) as a guide.
After removing the rear case shell and turning the device over (front
panel facing down), we see two green printed circuit boards (PCBs).
The largest one is at the bottom of the stack. It is fitted directly
to the front panel and holds the contacts for the keypad. In addition,
it covers the Liquid Crystal Display (LCD).
In the image below this board is highlighted with a blue outline.
Above the implant is a Li-ION battery pack that is connected to a 2-pin
header. It is used to power the implant when the telephone set is
disconnected from its power source. To the right of the implant are
the audio amplifiers (for the microphone and speaker signals) and
a circuit for charging the battery pack. At the bottom is the antenna
by which the device is connected to the Listening Post (LP) outside
the building. The LP had to be in the immediate vicinity of the bug.
When the telephone is reassembled, the implant and the additional parts
on the replacement keypad board (implant 1)
are virtually invisible, as they are obstructed from view by the main
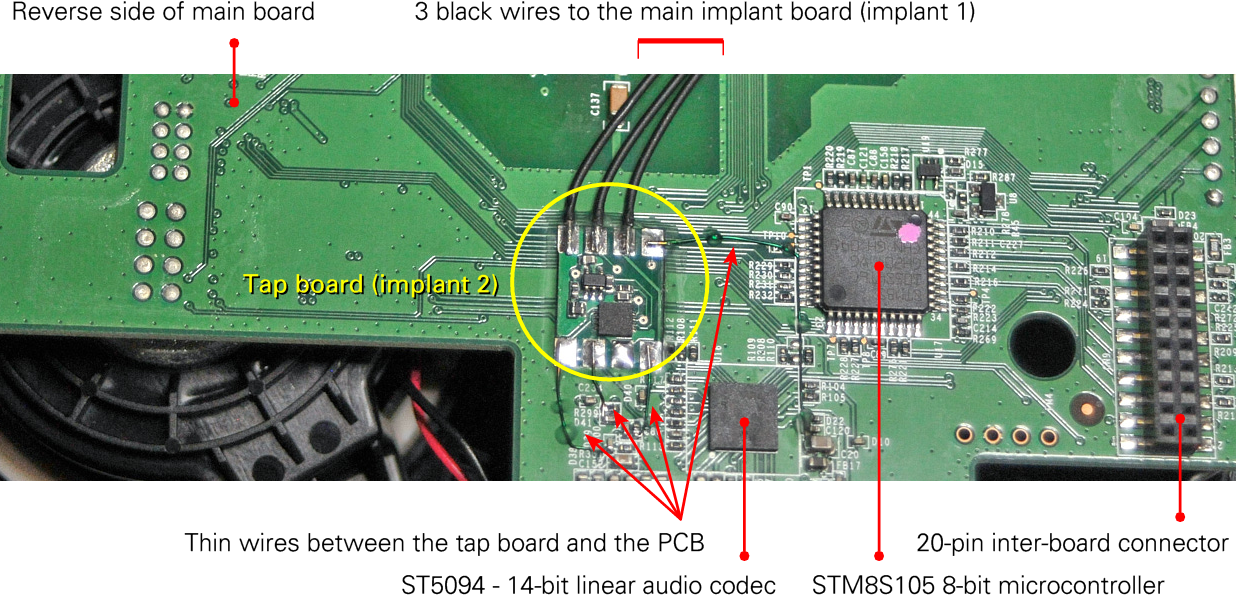
board. The tap board (implant 2)
is also invisible as it is at the rear side of the main board.
From the available photographs it is difficult to identify the various
components, in particular because the photographs are unsharp and the
implant PCB is covered by a conformal coating.
But some information can be gained from Andy Müller-Maguhn's
presentation on the subject [1].
All components have manufacturing date codes of April 2013 or earlier,
which implies that the implant was made after that date.
Furthermore, the dimensions of the board suggest a non-metric origin.
The antenna is dimensioned for operation at a UHF frequency on or
near 800 MHz.
It is difficult to determine who planted the bug in the
CryptoPhone IP-19,
but judging from its professional signature, the choice of components
and the no doubt high development cost, it seems likely that it was
a state actor. Furthermore, to plant the device, an operative had
to gain access to the premises where the phone was kept, which is
not without risk. Taking into account that the United States wanted
Assange
for violating the Espionage Act and revealing state secrets, it
seems likely the US
Central Intelligence Agency (CIA)
was behind the operation, probably with help from the US
National Security Agency (NSA)
and British intelligence service GCHQ
or MI5.
It is unknown how long the device had been in operation before it was
discovered, but this might have been years. The phone was first used
from the UK for confidential talks with the German magazine
Der Spiegel in mid-2013, in relation to the revelations of
NSA whistleblower Edward Snowden.
From the date codes on the components found in the implant, it
is certain that it was made some time after April 2013.
In theory it could have been inserted later that year or early in
2014, in which case it might have been operational for
The device is partly based on an existing (NSA?) product (the actual
implant in the metal case), but its carrier board — the replacement
keypad board — is specifically made for this type of telephone.
Such designs are typically made by the Tailored Access Operations
(TAO) unit of the US National Security Agency
(NSA) [6][7].
From the way the implant is installed — implant 2 and its thin wires
are glued to the main board — it can be concluded that
the intelligence agency responsible for planting the bug had to
get access to the premises at least twice: once to remove the telephone
and once to put it back. Such operations are typically carried out by
the Physical Access Group (PAG) of the Center for Cyber Intelligence
(CCI} of the CIA [8].
Below is an educated guess of the block diagram of the implant, based
on information provided by Andy Müller-Maguhn in a presentation
at CCC on 28 December 2020 [1]. At the bottom is a miniature
amplifier board (implant 2) that is soldered onto the main board of
the telephone set.
The other part of the bug (implant 1) is a large printed circuit board
(PCB) that replaces the existing keypad PCB of the telephone set.
It contains two amplifiers — one for the microphone circuit of the
telephone and one for the speaker circuit — a rechargeable Li-ION battery,
a patch antenna (part of the PCB) and a rectangular metal enclosure
that contains the actual bug.
When commanded by a nearby Command and Control transmitter, the data
from the Flash Memory device is converted to a digital wideband waveform,
and transmitted as a burst via a built-in transmitter,
via a patch antenna at the edge of the PCB. Also connected to the
antenna is the Command and Control receiver through which the listening
post (LP) can request the data.
The Li-ION battery, which is mounted on the large implant board and is
recharged by the telephone, allows the device to deliver its data even
when the telephone itself is disconnected. It is likely that the bug
is controlled by a (virtual) microcontroller that is part of one of
the FPGAs.
| |||||||||||||||||