
A new version of the Kronos banking trojan is making the rounds, according to Proofpoint security researchers, who say they've identified at last three campaigns spreading a revamped version of this old trojan that had its heyday back in 2014.
According to a report published yesterday evening, first samples of this new Kronos variant have been spotted in April, this year.
While initial samples appeared to be tets, real-life campaigns got off the ground in late June, when researchers started detecting malspam and exploit kits delivering this new version to users in the wild.
Campaigns targeted Germany, Japan, Poland
Proofpoint reports spotting three campaigns and one test run, targeting users of German, Japanese, and Polish banks.
| Period | Campaign type | Target | C&C |
|---|---|---|---|
| June 27-30, 2018 | Malspam, macro-laced Word docs | Users of 5 German financial institutions | http://jhrppbnh4d674kzh[.]onion/kpanel/connect.php |
| July 13, 2018 | RIG EK | Users of 13 Japanese financial institutions | http://jmjp2l7yqgaj5xvv[.]onion/kpanel/connect.php |
| July 15-16, 2018 | Malspam, CVE-2017-11882 | Users in Poland | http://suzfjfguuis326qw[.]onion/kpanel/connect.php |
| July 20, 2018 | Software download site | Test run | hxxp://mysmo35wlwhrkeez[.]onion/kpanel/connect.php |
The malware used in this campaigns is not the original Kronos, but one that received several updates compared to its 2014 edition [1, 2, 3, 4].
Proofpoint reports an extensive code overlap between the 2018 and 2014 versions. Similarities include that the 2018 version uses the same Windows API hashing technique and hashes, the same string encryption technique, the same C&C encryption mechanism, the same C&C protocol and encryption, the same webinject format (Zeus format), and a similar C&C panel file layout.
But the two versions are not identical. The main difference is that the 2018 edition uses Tor-hosted C&C control panels.
Kronos 2018 edition could be new Osiris trojan
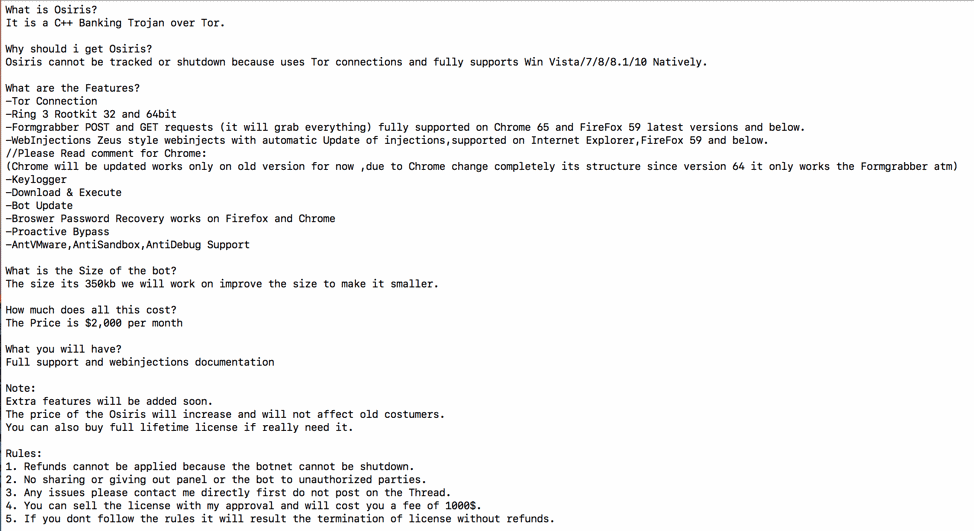
Researchers say that at the same time this new Kronos variant started appearing on their radar, a malware author started advertising a new banking trojan on hacking forums that he referred to as Osiris.
Proofpoint researchers did not manage to get their hands on a sample of this new Osiris malware, but they say the ad perfectly described the Kronos 2018 edition.
The biggest clue is that the author of this new trojan claims his trojan is only 350 KB in size, which is close to the (351 KB) size of an early Kronos 2018 edition sample researchers found in April. Coincidentally or not, that sample was named os.exe, presumably from Osiris, albeit not confirmed.
Kronos' reappearance comes as other banking trojans are also seeing a surge in activity after distribution efforts quieted down in 2017 and early 2018.
Security researchers Marcus Hutchins (aka MalwareTech) is facing legal charges in the US on allegations of having developed the 2014 edition of the Kronos banking trojan.
I'm still on trial for writing Kronos, meanwhile the real author is still updating the code https://t.co/pDYARvn0nk
— MalwareTech (@MalwareTechBlog) July 24, 2018
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.

