
Cybercriminals are using a new method to evade detection to make sure that the traffic generated by their malicious campaigns is not being detected, a technique based on SSL/TLS signature randomization and dubbed cipher stunting.
The vast majority of malicious traffic on the Internet — including attacks against web apps, scraping, credential abuse, and more — is funneled via secure connections over SSL/TLS says Akamai's Threat Research Team in a report published today.
Akamai's report says that "From an attacker's perspective, tweaking SSL/TLS client behavior can be trivial for some aspects of fingerprinting evasion, but the difficulty can ramp up for others depending on the purpose of evasion or the bot in question. In such settings, many packages require deep levels of knowledge and understanding on the attacker's part in order to operate correctly."
This technique is used by attackers to evade detection and run their malicious campaigns undisturbed, with at least a few tens of thousands of TLS fingerprints being used for such purposes before the novel cipher stunting evasion method was observed by the researchers.
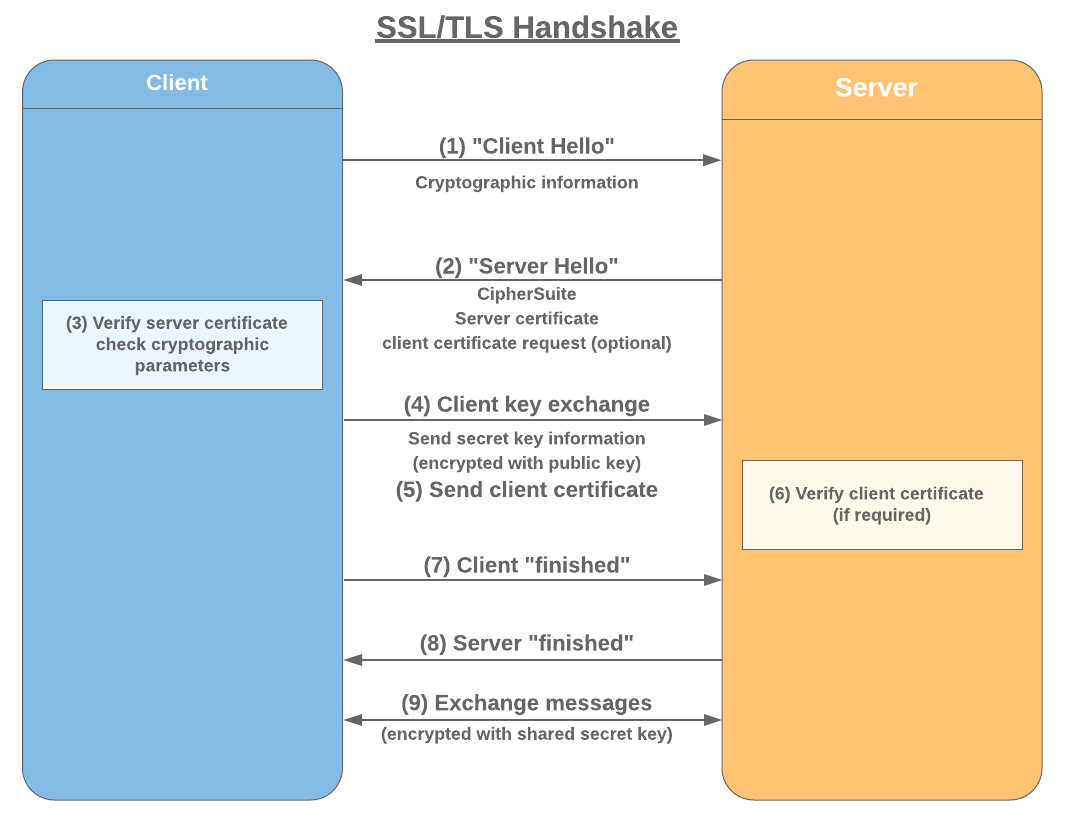
Akamai uses the Client Hello message delivered via clear text with each handshake as part of SSL/TLS negotiations for fingerprinting purposes, to "differentiate between legitimate clients and impersonators, proxy and shared IP detection, and TLS terminators."
"The TLS fingerprints that Akamai observed before Cipher Stunting was observed could be counted in the tens of thousands. Soon after the initial observation, that count ballooned to millions, and then recently jumped to billions," says Akamai.
More to the point, crooks who use SSL/TLS signatures to carry out malicious campaigns over secure connections have drastically increased their efforts lately, with random signatures observed in TLS tampering instances seeing a huge growth between September 2018 and February 2019.
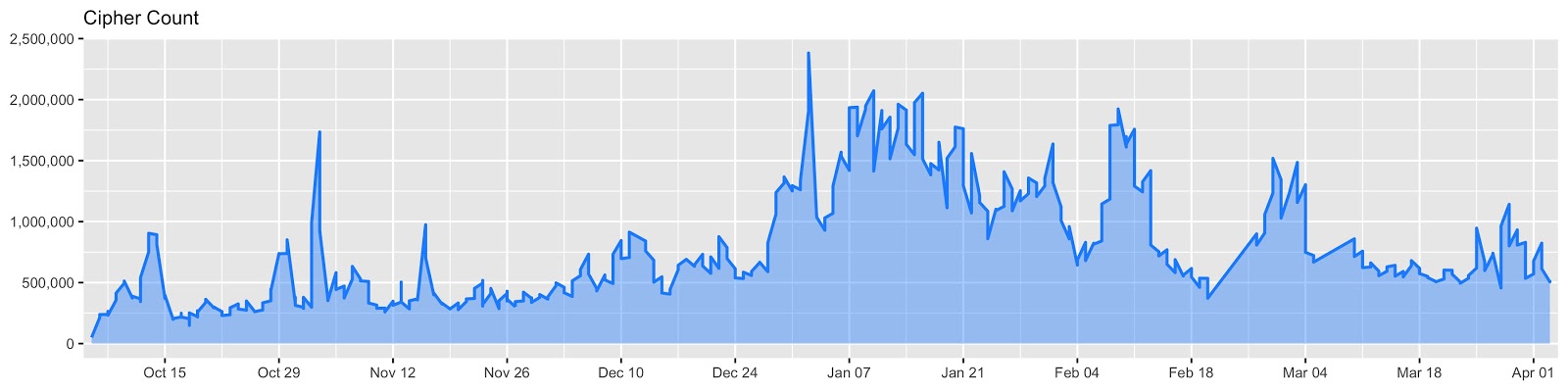
From 18,652 distinct fingerprints observed globally by Akamai in August 2018, after TLS tampering campaigns have started surfacing in early-September 2018 they reached a new high of 255 million instances during late-October following attacks "directed toward airlines, banking, and dating websites, which are often targets for credential stuffing attacks and content scraping."
The number of tampering instances detected by Akamai's research team globally reached an astounding number of 1,355,334,179 billion instances at the end of February 2019.
Those responsible are presenting a randomized cipher suite list in the 'Client Hello' messages, that in turn, randomize the hashes at the end. Additional analysis gives us the ability to hone and recognize important implementation details form the attacker. This is due to the relatively small and finite set of the SSL/TLS stack implementations available today. Each one allows for a different level of user intervention and customization of the SSL/TLS negotiation.
Akamai's Threat Research Team concludes by stating that "The key lesson here is that criminals will do whatever they can to avoid detection and keep their schemes going. The ability to have deep visibility over time into the Internet's traffic comes into play when dealing with these evolving evasion tactics."
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.

