Open Source Introducing new SigmaHQ Rule Packs
SIEM Detection Format
The shareable
detection format for
security professionals.
Get the most out of the Sigma ecosystem in your SIEM, and start using thousands of great security detections from the community and beyond.
aws_root_account_usage.yml
title: AWS Root Credentials description: Detects AWS root account usage logsource: product: aws service: cloudtrail detection: selection: userIdentity.type: Root filter: eventType: AwsServiceEvent condition: selection and not filter falsepositives: - AWS Tasks That Require Root User Credentials level: medium
![]()
sourcetype="aws:cloudtrail" userIdentity.type="Root" NOT eventType="AwsServiceEvent"
... or any supported SIEM.
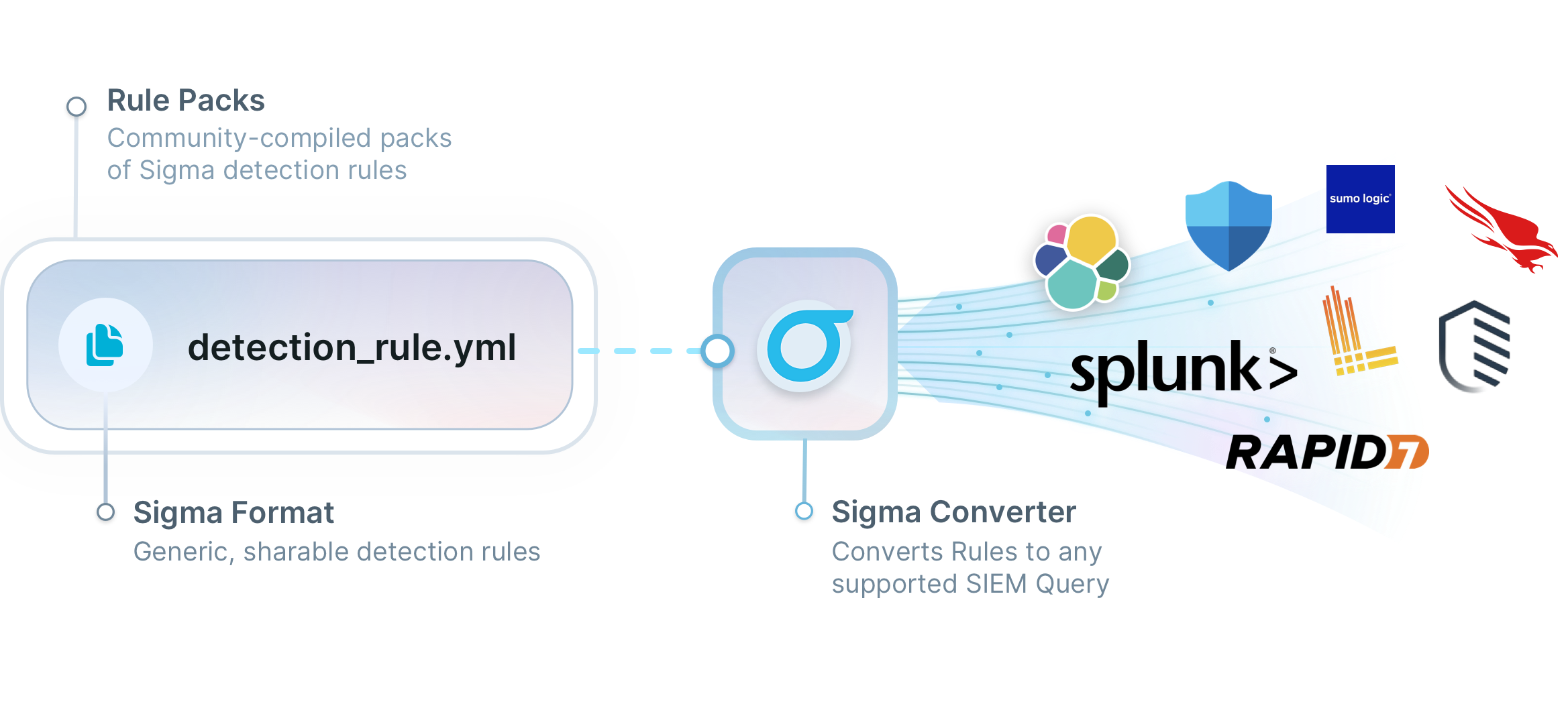
What is Sigma?
Share detectable malicious behaviour.
Sigma is a generic, open, and structured detection format that allows security teams to detect relevant log events in a simple and shareable way.
Learn more about Sigma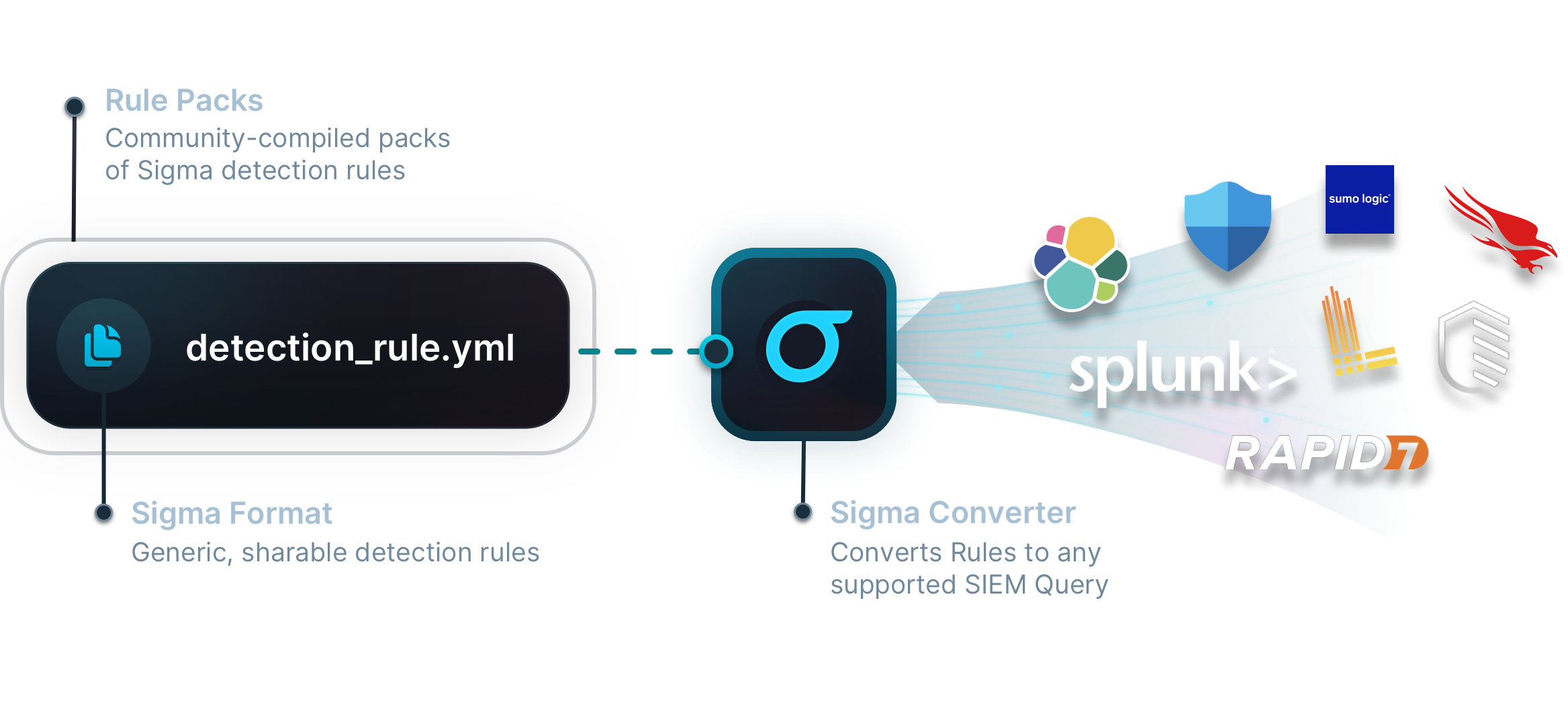
Learn
Explore the Sigma Ecosystem
Acknowledgements
Sigma would not be possible without the hard work and dedications of hundreds of online contributors through Github.
If you would like to support the project in any way, please visit our contribute guide on the sigma documentation page.