Previous parts:
When The New York Times first revealed TREASURE MAP in November 2013, the story focused on an NSA program that, according to the agency's own documents, created "a near real-time, interactive map of the global Internet" that could map "any device, anywhere, all the time." The capability sounded sweeping, but the emphasis was on mapping and visualization.
The full documents reveal additional purpose.
TREASURE MAP wasn't designed merely to observe the Internet and telecommunications infrastructure. The NSA's own documents, published by Der Spiegel in September 2014, listed the program's uses as including "Computer Attack/Exploit Planning." Networks marked in red on TREASURE MAP diagrams weren't just being monitored; they had been penetrated, fitted with what the documents call "SIGINT collection access points within AS." In intelligence terminology, these represent footholds for both surveillance and offensive operations.
Der Spiegel's 2014 reporting focused on what this meant for Germany: compromised satellite providers Stellar, IABG, and Ce-Tel; a regional ISP, Netcologne; and Deutsche Telekom. The story made headlines. It seemed comprehensive.
But a systematic analysis of the same documents reveals that the coverage missed at least 20 major telecommunications providers across three continents marked as compromised; networks penetrated, infrastructure accessed, routing systems mapped. The list includes providers in allied nations that were never named in any news report, such as TeliaNet (TeliaSonera), Verizon Business Europe, Singapore Telecommunications, Telecom Italia Sparkle, Cyprus Telecommunications Authority, TM Net, and TTNET (Turk Telekom).
Over a decade after publication, this is the (almost[note1]) complete list of network providers NSA and GCHQ had broken into based on the documents - a list that hasn't been reported elsewhere to our knowledge.
The company names and AS numbers appear on the list as they are documented in the source materials.
| Company name | AS | Countries / regions |
|---|---|---|
| CW Cable and Wireless plc | AS1273 | United Kingdom |
| CYTA-NETWORK Cyprus Telecommunications Authority | AS6866 | Cyprus |
| DE-IABG-TELEPORT IABG Teleport, DE | AS29259 | Germany |
| Deutsche Telekom AG | - | Germany |
| Gateway Communications | AS25395 | Belgium |
| GBLX Global Crossing Ltd. | - | Globally |
| Intelsat Global | AS22351 | United States |
| NETCOLOGNE NETCOLOGNE AS | AS8422 | Germany |
| NSS-UK New Skies Satellites UK AS | AS17175 | United Kingdom |
| NTT-COMMUNICATIONS NTT America, Inc. | - | Japan |
| PKTELECOM AS PK Pakistan Telecommunication Company Limited | AS17557 | Pakistan |
| PLANETSKY Planetsky Ltd. AS object | AS21455 | Cyprus |
| SHOWNET-KW-AS Shownet Internet Solutions Ltd | AS24627 | Kuwait |
| SINGTEL AS AP Singapore Telecommunications Ltd | AS7473 | Singapore |
| STELLAR-PCS-AS Stellar PCS GmbH, Germany | AS35207 | Germany |
| Telecom Italia Sparkle | AS6762 | Italy |
| TELIANET TeliaNet Global Network | AS1299 | Sweden, Finland |
| TMNET AS AP TMNet Internet Service Provider | AS4788 | Malaysia |
| TTNET TTnet Autonomous System | - | Turkey |
| Verizon Business Commercial IP service provider in Europe | AS702 | Europe |
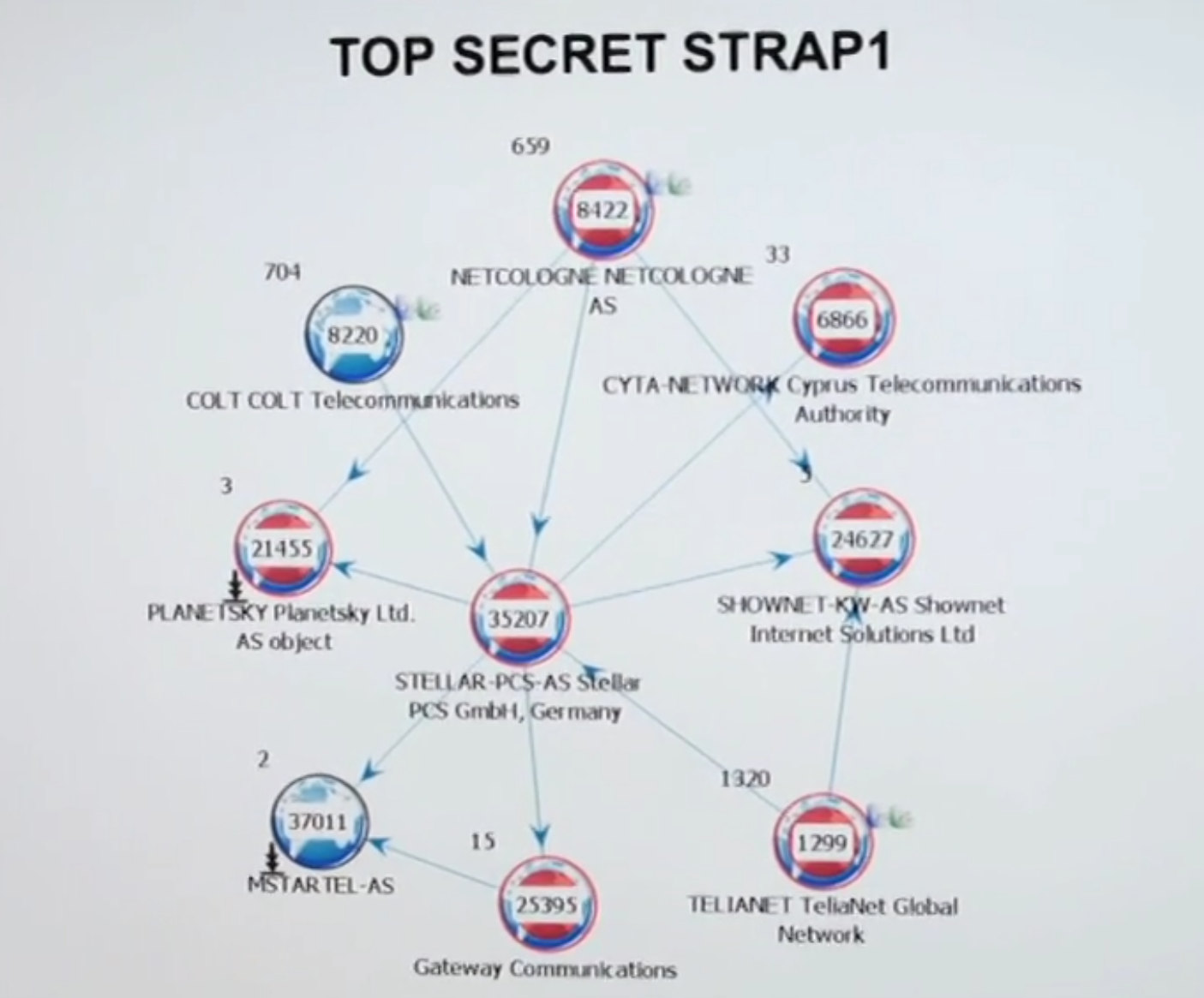
Screenshot from the Der Spiegel's Stellar video.
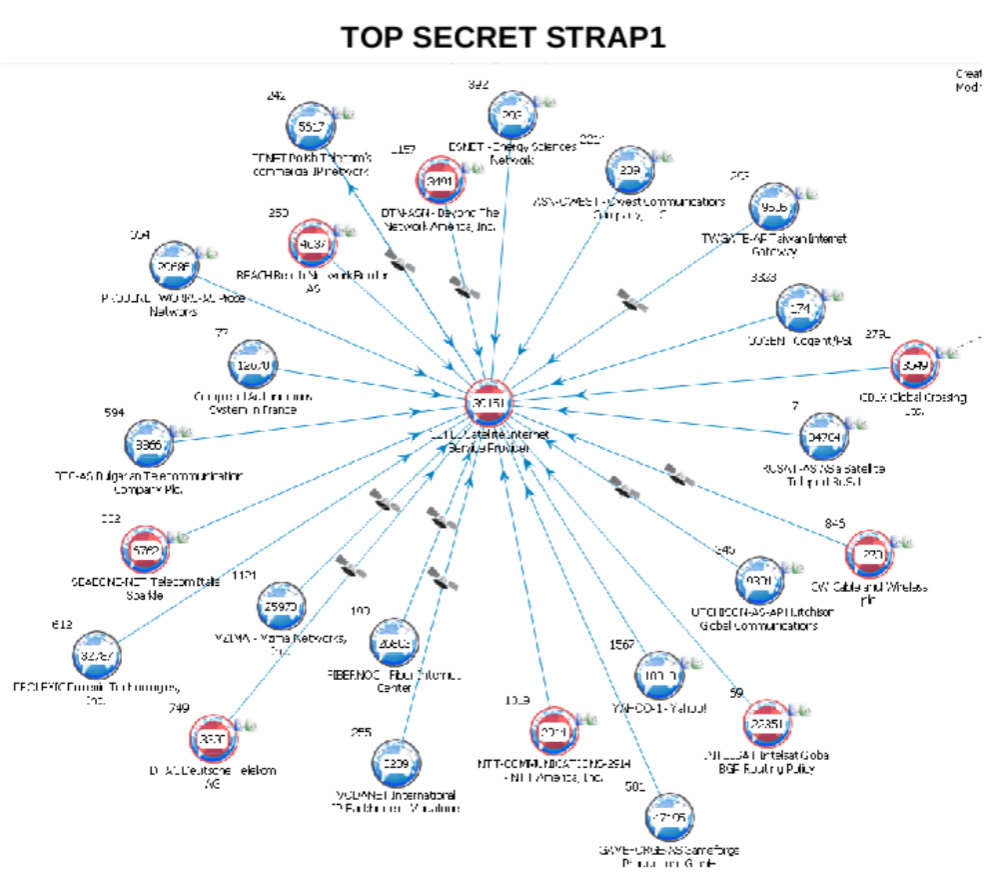
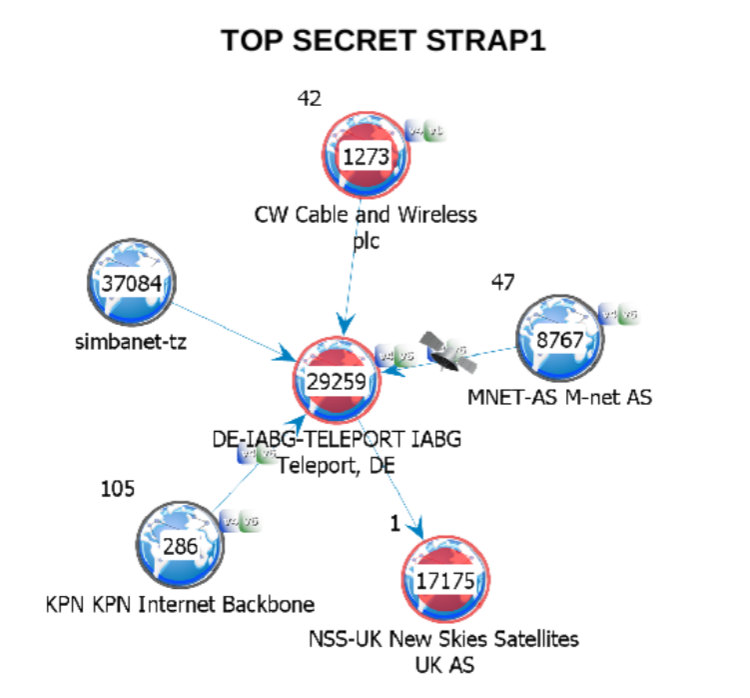
Additional providers marked as "Red Core Nodes". Page 12 and 17, SATELLITE TELEPORT KNOWLEDGE.
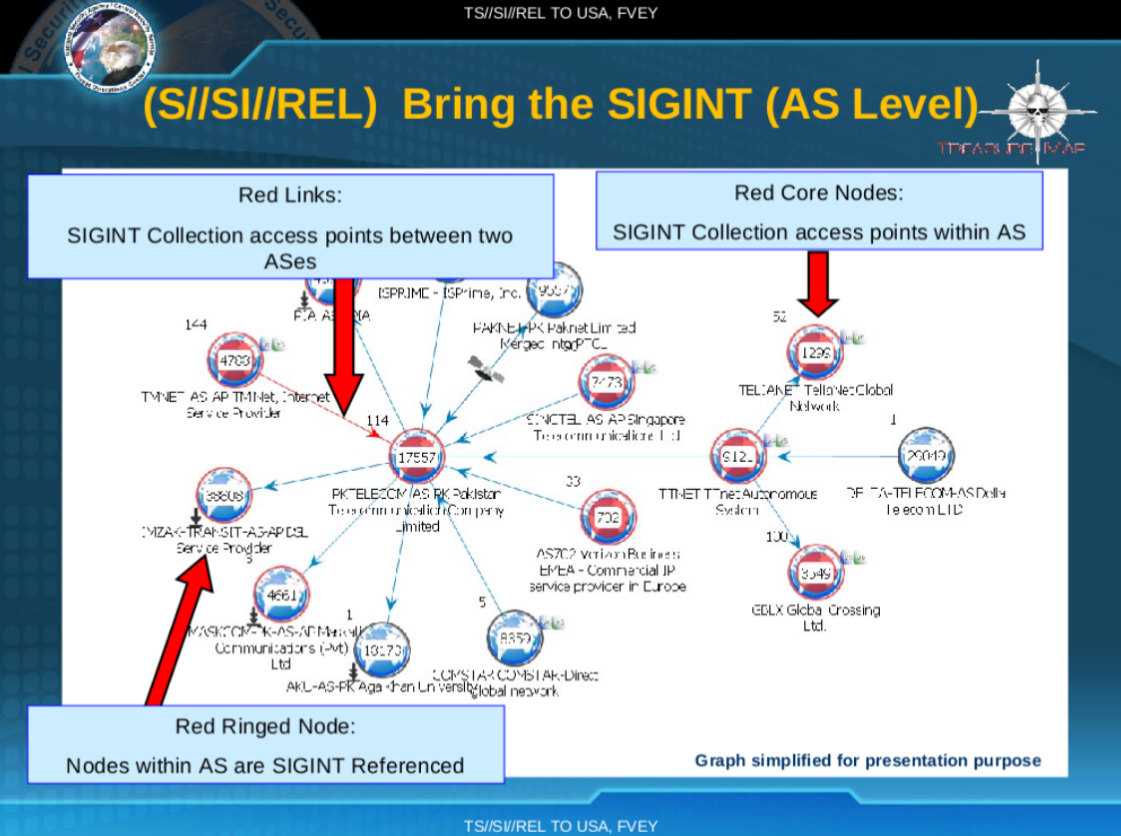
Additional "Red Core Node" providers shown on page 26 of the TREASURE MAP presentation "Bad guys are everywhere, good guys are somewhere!"
TREASURE MAP served dual purposes: mapping the global Internet infrastructure and identifying footholds for surveillance and offensive operations. The system aggregated data from multiple sources to create comprehensive network topology covering the entire Internet. Networks where NSA and GCHQ had established "SIGINT collection access points" through Computer Network Exploitation (CNE) operations were marked as "Red Core Nodes."
Feeding the machine
In addition to penetrating the telecommunications carriers listed above, TREASURE MAP mapped the broader Internet infrastructure using data from multiple sources.
Network measurement data: The system ingested approximately 16-18 million traceroutes daily from sources including CAIDA's academic Archipelago project (~10 million traceroutes/day).
PACKAGEDGOODS covert servers (~6.5 million/day from 13 "unwitting datacenters around the globe"), and commercial providers including Akamai.
Signals intelligence: At least 15 classified collection programs fed TREASURE MAP, including BLACKPEARL (SIGINT session data and router identification), DISCOROUTE (router configuration files from CNE and passive collection), MASTERSHAKE (satellite and WiFi intercepts), and JOLLYROGER (metadata from TAO-implanted computers).
Additional sources: BGP routing data from public and commercial sources, DNS records, IP geolocation data, WiFi network information, VPN endpoints, and operating system fingerprints covering 30-50 million unique IP addresses daily.
Botnets
A May 2010 document describes (p. 25) an additional source: compromised botnet computers. Under an operation codenamed DEFIANTWARRIOR, NSA used "hostile takeover" techniques to take control of criminal and foreign botnets. The compromised computers were repurposed to conduct traceroutes across the Internet, with results feeding directly into TREASURE MAP.
The document describes using "QUANTUMBOT" techniques: leveraging TURMOIL (passive collection platforms) to identify botnet traffic, then TURBINE (active injection systems) to send man-on-the-side packets taking control of the bots. As of May 2010, the operation had acquired hundreds of bots across multiple countries.
The depth of collection
Beyond network-level topology, TREASURE MAP compiled device-level intelligence. A 2010 Cisco Discovery Protocol (CDP) report shows the granularity.
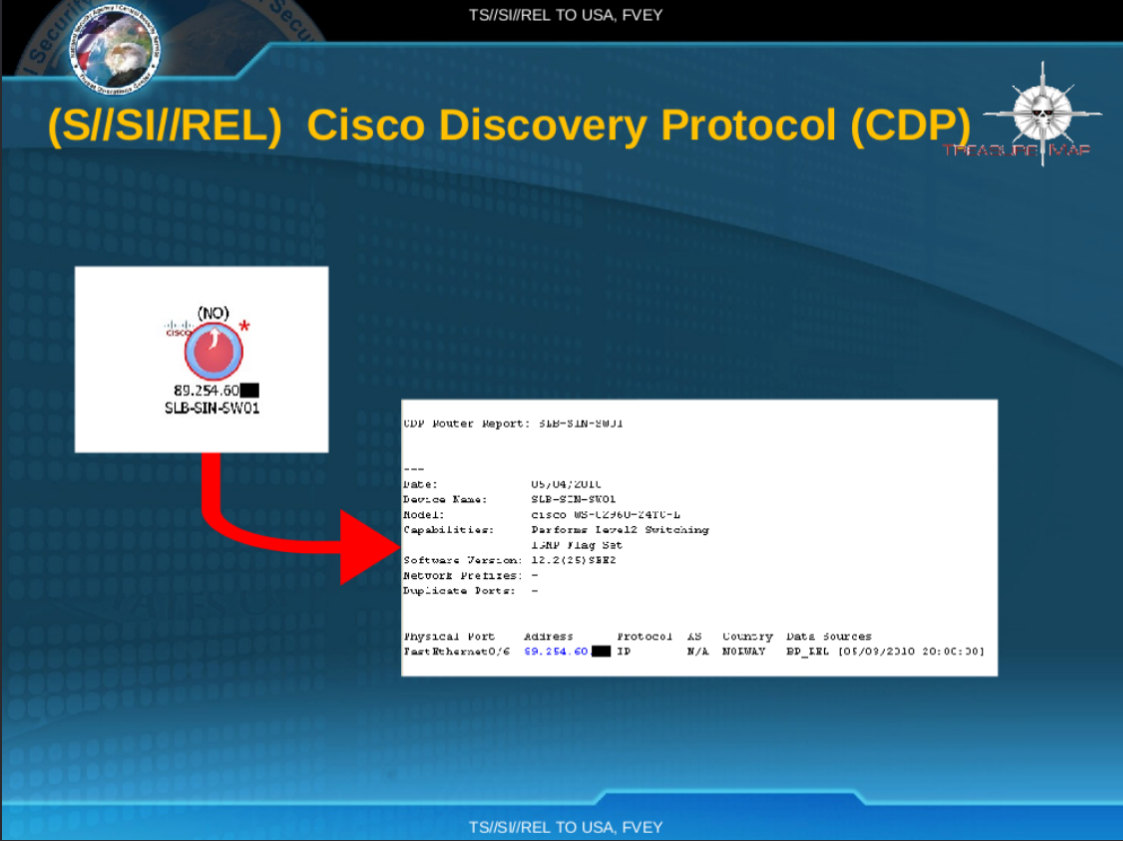
"Bad guys are everywhere, good guys are somewhere!" document page 30
In addition to the autonomous systems marked red, the documents include device-level evidence of network penetration. A Cisco Discovery Protocol (CDP) report dated May 3, 2010, identifies a network switch at IP address 89.254.60.[REDACTED] in Norway marked as being compromised.
The device is identified as a Cisco WS-C2960-24TC-L switch performing "Level 2 Switching", meaning it operates at the data link layer of the network, typically used for local infrastructure within a building or facility rather than backbone routing. The IP address falls within the range 89.254.0.0 to 89.254.63.255, which in 2010 was allocated to Schlumberger Information Technology Services Norge AS.
Schlumberger (SLB) is the world's largest oilfield services company, providing technology and infrastructure to the petroleum industry globally. In Norway, this would include communications infrastructure serving North Sea oil operations, offshore platforms, and drilling activities.
The entry provides detailed visibility into the device: exact model number, software version, physical port configuration, and network topology. This level of detail indicates active network reconnaissance.
The data source is listed as starting with "BP_". Based on naming patterns in the TREASURE MAP documents, "BP" likely refers to BLACKPEARL, an NSA signals intelligence tool described in the documents providing "SIGINT session 5-tuple, identified routers, routing protocols, SIGINT access points." Other leaked NSA documents describe BLACKPEARL as enabling automated linking of DNI (Digital Network Intelligence) information and network characterization against survey collection across the SIGINT system, producing reports on VPNs, network access points, and router configurations. The tool was designed for finding access or gathering information on a network an analyst was assessing.
But how?
Other Snowden documents indicate these access points were established through CNE operations. TREASURE MAP was part of NSA's standard CNE analysis toolkit. An October 2009 NSA presentation lists TREASURE MAP under CNE analytic projects processing network data. The presentation describes CNE collection as yielding "config files, registry, network information" - the router configurations visible in the documents.
Training materials for SIGINT development analysts listed TREASURE MAP as a routine tool alongside database systems like DISCOROUTE, BLACKPEARL, and XKEYSCORE.
The specific techniques used aren't detailed in the documents. Der Spiegel's 2014 investigation contacted the compromised companies to inform them of the penetrations. The reactions indicated the companies were unaware: Stellar's CEO responded "Fuck!" when shown evidence of GCHQ access. Deutsche Telekom stated "The accessing of our network by foreign intelligence agencies would be completely unacceptable." Security teams at both Deutsche Telekom and Netcologne conducted investigations but found no suspicious mechanisms or data streams.
Der Spiegel contacted 11 non-German providers marked in the documents. Four responded, all saying they examined their systems and found no irregularities.
The inability of targeted companies' security teams to detect the compromise suggests sophisticated CNE techniques that either left no forensic traces or were cleaned up after access was established.
CNE operations against telecommunications infrastructure can employ multiple techniques.
Covert technical exploitation: NSA and GCHQ could use sophisticated hacking techniques to penetrate the networks without any insider knowledge. The agencies are known to exploit vulnerabilities in routers, networking equipment, and management systems. Documents describing operations against Belgacom showed GCHQ using advanced exploitation techniques (QUANTUM INSERT attacks) to compromise employee computers, then pivoting to internal network infrastructure. Similar techniques could explain router-level access without company cooperation.
Insider cooperation: Access could be facilitated by individuals within the targeted companies, either willing intelligence assets or compromised employees. A single insider with the right credentials could provide configuration files, access credentials, or create backdoors for persistent access. This wouldn't require management awareness and would be nearly impossible for security teams to detect if the insider maintained operational security.
Covert corporate cooperation: Some companies might have provided access under legal compulsion, national security letters, or intelligence agreements they cannot publicly acknowledge.
Government-facilitated access: National intelligence services in the countries where these companies operate could have provided NSA/GCHQ with access to domestic telecommunications infrastructure as part of intelligence-sharing arrangements. Sweden's FRA (Försvarets radioanstalt), for instance, has long cooperated with NSA. If Swedish intelligence had legal access to TeliaSonera's network, they could have shared that access with Five Eyes partners. This would probably be legal under Swedish law but would likely remain classified.
Supply-chain interdiction: NSA's TAO unit is known to intercept networking equipment during shipping to install backdoors before devices reach customers. If routers or switches deployed by these telecommunications providers had been compromised before installation, the companies themselves might be genuinely ignorant of the access. Documents published by Der Spiegel in December 2013 showed NSA maintaining an "Advanced Network Technology" (ANT) catalog of equipment implants and techniques for this purpose.
Third-party management systems: Many telecommunications companies use third-party network management platforms, monitoring systems, or cloud-based infrastructure management tools. If NSA/GCHQ compromised these intermediary systems, they could gain visibility into multiple networks simultaneously without directly penetrating each company's infrastructure.
The scale and persistence of access across 20+ major providers, including multiple state-owned carriers, suggests a combination of these CNE techniques. The documents distinguish between "Red Core Nodes" (collection access points within autonomous systems) and "Red Links" (collection access points between autonomous systems), indicating both router-level access inside networks and access to inter-network connections.
What remains unclear is which specific CNE techniques were used for which targets, whether any access was authorized by governments who never informed their own state-owned telecommunications companies, and whether these access points remain active today.
Who had access - Beyond NSA and GCHQ
The TREASURE MAP documents reveal the system operated on three separate classified networks, indicating access extended well beyond NSA and GCHQ:
-
NSANet - The NSA's internal network, shared with Five Eyes partners.
-
JWICS (Joint Worldwide Intelligence Communications System) - Used by the entire U.S. Intelligence Community, including CIA, DIA, FBI, and 15 other agencies.
-
SIPRNet (Secret Internet Protocol Router Network) - The Department of Defense's classified network, accessible to military intelligence across all service branches.
-
A 2011 internal NSA newsletter announced a new TREASURE MAP release, stating: "Everyone with access to NSANet or Intelink with a valid PKI certificate can access the system."
This meant the penetrated telecommunications networks weren't just targets for NSA or GCHQ signals intelligence operations. The compromised infrastructure was mapped and accessible to analysts across the U.S. military and intelligence apparatus.
What remains unknown
-
Whether affected governments knew their state-owned carriers were compromised.
-
Whether any access was legally authorized through intelligence-sharing arrangements.
-
Whether companies were genuinely ignorant or covertly complicit.
-
Whether these access points remain active today.
-
What data was collected and how it was used, and how the "access points" themselves were used.
Der Spiegel's 2014 reporting identified compromised German providers and noted that 11 non-German providers[note2] were also marked in the documents, but the article focused on the domestic German angle. No subsequent reporting identified the non-German networks.
The published documents, despite degraded image quality in some pages, contain identifiable AS numbers and company names for at least 20 networks marked as compromised.
The systematic compromise of allied telecommunications infrastructure documented in these materials represents a significantly broader operation than was publicly reported. The scope - spanning NATO members, Five Eyes partners' neighbors, and state-owned critical infrastructure across three continents - went unreported for over a decade.
Documents
Primary documents
- SATELLITE TELEPORT KNOWLEDGE
- Bad guys are everywhere, good guys are somewhere!
- 2011 internal NSA newsletter
Notes
[note1]: Some AS numbers and company names can't be definitively identified due to document quality.[↑back up]
[note2]: The published documents show at least 16 non-German providers marked as "Red Core Node", not 11 as Der Spiegel reported.[↑back up]