We are seeing a large number of WordPress sites compromised with the “visitorTracker_isMob” malware code. This campaign started 15 days ago, but only in the last few days have we started to see it gain traction; really affecting a large number of sites.
Here is a quick snapshot of what we’re seeing with the infection rates over the past two weeks, but the most interesting trend is over the past 48 hours, as it has grown significantly. These are the daily infection rates:
We initially shared our thoughts on it via our SucuriLabs Notes, but as the campaign has evolved we have been able to decipher more information as we investigate the affects on more compromised sites. This post should serve as a resource to help WordPress administrators (i.e., webmasters) in the WordPress community.
Technical Description
This malware campaign is interesting, its final goal is to use as many compromised websites as possible to redirect all their visitors to a Nuclear Exploit Kit landing page. These landing pages will try a wide variety of available browser exploits to infect the computers of unsuspecting visitors.
If you think about it, the compromised websites are just means for the criminals to get access to as many endpoint desktops as they can. What’s the easiest way to reach out to endpoints? Websites, of course.
This malware campaign adds the following code to all javascript files on the site:
function visitorTracker_isMob( ){
var ua = window.navigator.userAgent.toLowerCase();
if(/(android|bb\d+|meego).+mobile|avantgo|bada\/|blackberry|blazer|compal|elaine|fennec|hiptop|iemobile|ip(hone|od)|iris|kindle|lge |maemo|mi..|v400|v750|veri|vi(rg|te)|vk(40|5[0-3]|\-v)|vm40|voda|vulc .. |vx(52|53|60|61|70|80|81|83|85|98)|w3c(\-| )|webc|whit|wi(g |nc|nw)|wmlb|wonu|x700|yas\-|your|zeto|zte\-/i.test(ua.substr(0,4))) {
return true;
return false;
} /* .. visitorTracker .. */ /*
Which interacts with a secondary backdoor inside the site to force the browser to load a malicious iframe from one of their Nuclear Exploit Kit landing pages. The current landing page is pointing to vovagandon.tk (193.169.244.159), but that domain changes very often.
We named this malware campaign “VisitorTracker“, because of the function name used in all injected javascript files: visitorTracker_isMob().
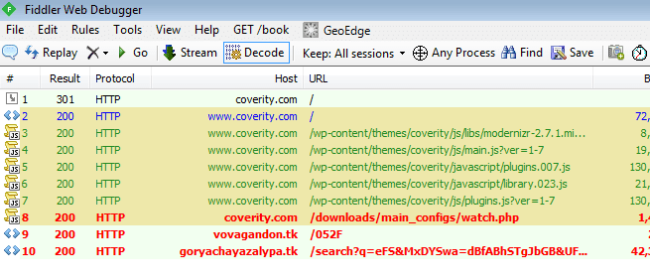
At the network level, here is what you would see when visiting a compromised site (thanks to Jerome Segura from MalwareBytes for sharing this with us):
In this case, a large security provider (Coverity) has their site hacked and you can see the iframe being loaded and the browser connecting being sent to the exploit kit landing page at vovagandon.tk. We already reached out to Coverity about the issue, and they should be addressing it soon.
Protect your sites!
We detected thousands of sites compromised with this malware just today and 95% of them are using WordPress. We do not have a specific entry point determined yet, but it seems to be a campaign targeting latest vulnerabilities in plugins. Out of all the sites we detected to be compromised, 17% of them already got blacklisted by Google and other popular blacklists.
If you are a WordPress user, make sure you keep all your plugins updated, including premium ones. I also recommend checking your site via our Free Security / Malware Scanner (SiteCheck) to verify if you’re currently being affected by this campaign. If you’re a system administrator and have access to your server you can use the following command (grep) to search for the infection on your files:
grep -r “visitorTracker_isMob” /var/www/
Once identified, we recommend you proceed with removing the infection and looking for any other indicators of compromise. If you need professional response, our team is standing by to assist.
Daniel B. Cid is Founder of Sucuri and the VP of Engineering for the GoDaddy Security Products group. He is also the founder of OSSEC and CleanBrowsing. You can find more about Daniel on his site dcid.me or on Twitter: @danielcid