NSA officials wrote:
Many organizations use enterprise DNS resolvers or specific external DNS providers as a key element in the overall network security architecture. These protective DNS services may filter domains and IP addresses based on known malicious domains, restricted content categories, reputation information, typosquatting protections, advanced analysis, DNS Security Extensions (DNSSEC) validation, or other reasons. When DoH is used with external DoH resolvers and the enterprise DNS service is bypassed, the organization’s devices can lose these important defenses. This also prevents local-level DNS caching and the performance improvements it can bring.
Malware can also leverage DoH to perform DNS lookups that bypass enterprise DNS resolvers and network monitoring tools, often for command and control or exfiltration purposes.
There are other risks as well. For instance, when an end-user device with DoH enabled tries to connect to a domain inside the enterprise network, it will first send a DNS query to the external DoH resolver. Even if the request eventually fails over to the enterprise DNS resolver, it can still divulge internal network information in the process. What’s more, funneling lookups for internal domains to an outside resolver can create network performance problems.
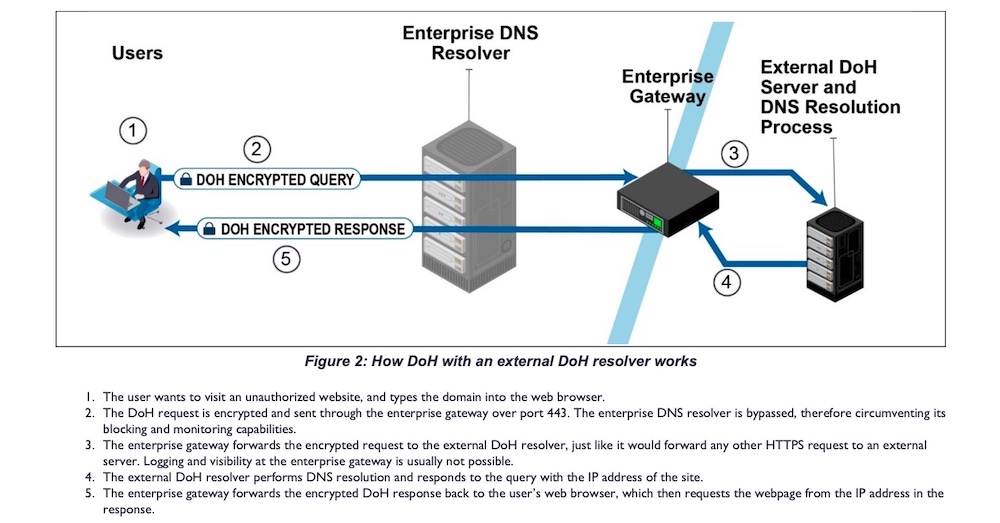
The image immediately below shows how DoH with an external resolver can completely bypass the enterprise DNS resolver and the many security defenses it may provide.
Credit: NSA
Bring your own DoH
The answer, Thursday’s recommendations said, are for enterprises wanting DoH to rely on their own DoH-enabled resolvers, which besides decrypting the request and returning an answer also provide inspection, logging, and other protections.
The recommendations go on to say that enterprises should configure network security devices to block all known external DoH servers. Blocking outgoing DoT traffic is more straightforward, since it always travels on port 853, which enterprises can block wholesale. That option isn’t available for curbing outgoing DoH traffic because it uses port 443, which can’t be blocked.
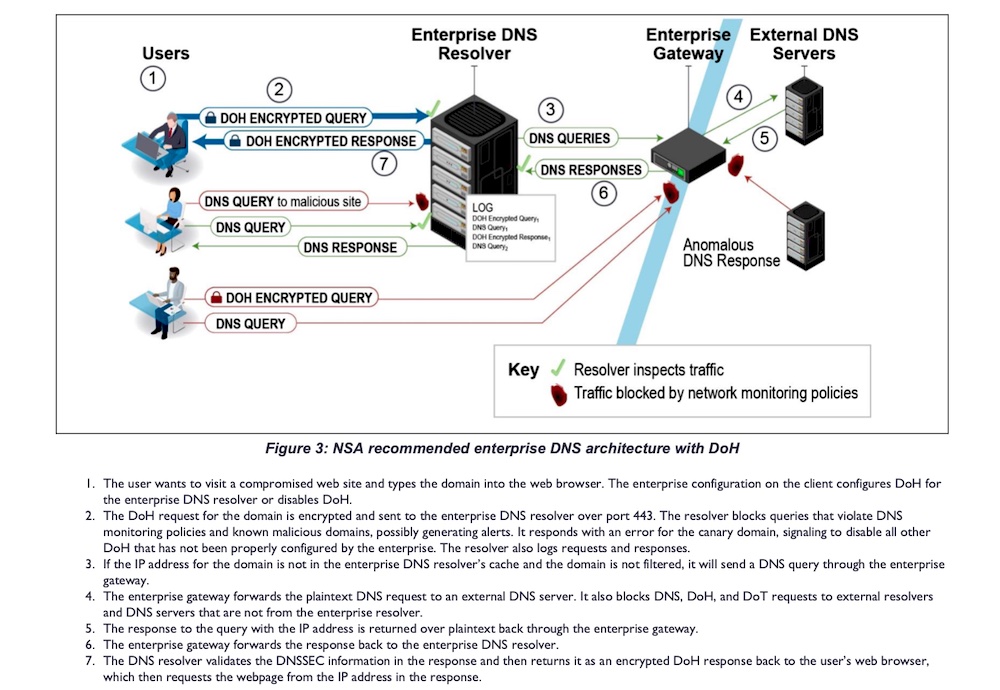
The image below shows the recommended enterprise set up.
Credit: NSA
DoH from external resolvers are fine for people connecting from home or small offices, Thursday’s recommendations said. I’d go a step further and say that it’s nothing short of crazy for people to use unencrypted DNS in 2021, after all the revelations over the past decade.
For enterprises, things are more nuanced.