People in 404 Celebrating Chinese New Year
1. The City That Didn\u2019t Exist
In my childhood bedroom, a glossy map of China hung on the wall. I used to believe it showed our factory area, the 404. On that map, I saw Shanxi, where my father was from, and the Northeast, my mother\u2019s home. Our neighbors had roots in Shandong and Shanghai.
At age three, I would trace the map with my small finger, trying to find 404\u2019s Central Park or the Workers\u2019 Club. I couldn\u2019t find them. I assumed the large blue patch was my home, and the green patch belonged to my friend upstairs.
In reality, Factory 404 was not marked on any map.
Years later, when I first used the internet and saw \u201C404: Page Not Found\u201D pop up on a screen, I was genuinely perplexed. How did the computer know that \u201C404\u201D couldn\u2019t be found\uFF1F
Located west of the Yumen Pass, 404 was a secret society hidden in the Gobi Desert. In 1958, the state mobilized thousands to build this oasis for the radioactive industry. Conditions were brutal. Sandstorms were a daily reality. The early settlers dug holes in the ground and covered them with thatch just to survive the nights. To this day, the name of our railway station remains \u201CDi Wo Pu\u201D\u200A\u2014\u200Awhich literally means \u201CLow-Lying Hollow.\u201D
Water was scarce. With only 50 millimeters of annual rainfall, drilling for wells was futile. Initially, water had to be trucked in, costing as much as gasoline. There wasn\u2019t a single tree, only scattered camel grass. When construction workers took their children to the nearest town, Yumen, the kids would point at a real tree and scream, \u201CLook! Giant camel grass!\u201D
Even years later, the sandstorms persisted. Small stones were lifted by the wind and painfully hit our faces. Sometimes the sky turned tangerine color. When the storm finally settled, the ground was blanketed in a layer of dust. Every step kicked up a puff of fine powder.
The first generation of 404 were the country\u2019s brightest elites. We had locksmiths who could replicate a key just by glancing at it, and lathe operators who could diagnose a machine\u2019s fault with their eyes closed. It wasn\u2019t just engineers. There were top-notch chefs and pastry masters drawn from major cities. To this day, the taste of the cream pastries I ate as a child remains a vivid memory\u200A\u2014\u200Aa sweet luxury in the middle of a barren desert.
But the most crucial hands belonged to the machinists. At that time, sophisticated CNC machines didn\u2019t exist, yet the core components of an atomic bomb required a level of precision that bordered on the impossible. The final, most delicate cuts were executed by human hands manually guiding the machine tools, maintaining a margin of error within 1/80th the width of a human hair.
The legendary \u201Cfinishing touches\u201D were performed by Yuan Gongpu, a master lathe operator recruited from the Shanghai Automobile Chassis Factory. His story was typical of that generation: he had just gotten married in Shanghai in April, only to be whisked away to the desolate Northwest in August.
During the \u201CThree Years of Hardship\u201D (1959\u20131961), when more than 30 million people across China starved to death, our factory area faced a desperate crisis. At one point, there were only a few days\u2019 worth of rations left in the warehouses, and workers began to suffer from severe edema due to malnutrition.
Deep in the Northwestern hinterland, transportation was notoriously difficult, so the factory decided it had to survive on its own. They established a farm to grow their own grain and vegetables. They channeled melting snow and ice from the Qilian Mountains for water, and organized hunting teams to venture deep into the mountains to bring back meat.
Gradually, the factory area achieved self-sufficiency. As life improved, 404 grew into a fully functioning city. It built its own department stores and cinemas, and even established dedicated factories just to produce vinegar and popsicles. By the time I was born, this small enclave of fewer than 30,000 people even boasted its own zoo.

In my childhood, I used to spend time in the zoo
2.The Radioactive Sofa
The initial slogan proposed during the establishment of 404 was: \u201CDedicate your youth, dedicate your life, and dedicate your descendants.\u201D
I am that descendant\u200A\u2014\u200Athe third generation. I was born in 1991, thirty years after China\u2019s first atomic bomb explosion, and right around the time of the dissolution of the Soviet Union.
By then, the city\u2019s mission had shifted. With the bomb long finished, 404 had transformed into a massive processing center for nuclear waste. Spent fuel rods from nuclear power plants across the country were transported here, where they were submerged in deep cooling pools for reprocessing.
Despite its remote location in the desert, 404 held a strange political prestige. When the weather forecast aired on provincial TV, the capital, Lanzhou, was mentioned first. The second city was always the \u201CGansu Mining Area\u201D\u200A\u2014\u200Athe code name for 404.
Our license plates started with \u201CGan-A,\u201D the same as the provincial capital. We laughed at people from other cities like Jiayuguan (\u201CGan-B\u201D) or Jiuquan (\u201CGan-F\u201D). Even as kids, we joked, \u201CWe\u2019re still number one.\u201D Because our grandparents were the country\u2019s elite and we lived in the \u201CNuclear City,\u201D I always felt like I was living at the center of the world.
But there was a darker side to this status. Because of the radioactive materials, our residential area was separated from the factory by an hour-long train ride.
The most dangerous job was \u201Cworking in the pit.\u201D Shifts there were strictly limited to thirty minutes to minimize radiation exposure. Workers had to shower and change into protective gear immediately after their shifts. As kids, most of us had never seen the factory; our parents simply described it as \u201Cdirty.\u201D
Occasionally, we heard whispers about accidents\u200A\u2014\u200Ahair falling out overnight, or leaks caused by local farmers digging up buried chemical drums and protective gear. Once, a soldier entered the residential area after coming into contact with radioactive material. His hands turned a necrotic black, like charred wood. The authorities didn\u2019t just isolate him; they traced his entire trajectory and burned every single item he had touched. A friend of my father lost his entire sofa because of this. Witnessing such scorched-earth containment makes the modern definition of nuclear power as the \u2018cleanest energy\u2019 completely incomprehensible to me.
Our life in the residential area was anchored by the Workers\u2019 Club and the department store. The town was small\u200A\u2014\u200Aless than two kilometers from end to end\u200A\u2014\u200Aand bookended by parks: a fishpond in the north and a zoo in the south.
My home was in the north, near the tallest structure in town: the Communication Building. It was a seven-story tower topped with a massive four-sided clock. No matter where you stood in the factory area, you could see the time and hear its chimes ringing across the desert.
Both my parents worked nearby. Just south of my home, past the Communication Building, was the bank. A stone\u2019s throw east of that was my kindergarten.
When I was three and a half, my mother took me to Beijing for her studies. It was my first time leaving the desert. I remember jumping for joy inside the train carriage. When we reached Tiananmen Square, I was overwhelmed. I ran wild, waving a red inflatable toy hammer. I became a spectacle myself\u200A\u2014\u200Aa group of foreign tourists sat on the ground and pulled me over to take photos, unaware they were posing with a child from a secret nuclear city.
Subscribe now
3. Pigs in Kindergarten
After returning from Beijing to 404, I was sent to the kindergarten.
The kindergarten was housed in a small, Western-style villa. While we sat inside the classroom, pigs roamed freely in the yard outside. Through the window, we could watch them rooting through the dirt. It was a perfect cycle: we ate the pigs, and the pigs ate our leftovers.
I couldn\u2019t stomach the fatty meat, so whenever the teacher wasn\u2019t looking, I would squeeze it in my hand and secretly stash it in my pocket. My mother only discovered this habit when she did the laundry. A few days later, when I visited the kindergarten teacher\u200A\u2014\u200Awho happened to be a former colleague of my mother\u200A\u2014\u200AI hid behind my mom\u2019s leg and confessed that I didn\u2019t like pork. The teacher smiled. The next day, the cafeteria served radish and vermicelli dumplings.
There was a formidable female teacher at the kindergarten. Unrequited love had driven her mad. Yet, strangely, we children weren\u2019t afraid of her. When she struck the ground with a long bamboo pole to demand silence, some kids would simply climb up the pole, giggling. The factory area was a sealed-off world; she wasn\u2019t the only one whose mind cracked under the strain of isolation and failed relationships. Later, her hair turned half-white and she grew heavy. She wandered the streets every day, yet the kindergarten continued to pay her salary.
My home life had its own rhythm: my father was often out playing mahjong at friends\u2019 houses, leaving my mother and me at home. While she was studying for a college exam, I played alone in my bedroom, weaving stories with my toys, emerging every hour just to ask her how the studying was going.
My biggest dream in kindergarten was to be a big brother. I wanted to care for a younger sibling. But under the One-Child Policy, if my mother had another child, she and my dad would lose their jobs. She had to follow the rules and terminate a pregnancy. My wish was impossible.
Whenever I felt unhappy, I would climb up to the second-floor terrace of the kindergarten, lift my shirt, and press my bare belly against the icy stone wall. I would whisper to myself, \u201CBig brother wants to go home.\u201D As the cold seeped into my skin, I would pull my shirt down, letting my body warmth return. This physical sensation\u200A\u2014\u200Afrom freezing to warm\u200A\u2014\u200Asomehow soothed my longing to be an older brother. But as a result, my digestion deteriorated, and my once-chubby figure withered into a skinny little bamboo stick.
My best friend lived upstairs. (We would eventually be neighbors for 13 years.)
Back in kindergarten, when she was in the Senior Group (the \u2018Big Class\u2019), I was still in the Middle Group. After lunch, I would spot her in the playroom across the hall and shout that I wanted to be in the Senior Group, too.
My mother pulled some strings with a former colleague, allowing me to move up a level early to join her. During nap time, our little beds were right next to each other. We would clutch candy wrappers in our hands, giggling endlessly. The teacher would scold us for disturbing the nap, but we Hid behind our parents, still laughing.
There was another boy in the neighboring unit, and the three of us often played under the acacia tree in front of our building. At four or five years old, I was deeply troubled by a serious question: which of us would eventually marry her?
After all the pigs in the backyard were consumed, I graduated from kindergarten and entered elementary school.
My elementary school was right next to the kindergarten. In front of the gates stood raised square concrete blocks\u200A\u2014\u200Aentrances to the air-raid shelters. In our factory town, these entrances were everywhere: at schools, residential buildings, and hospitals. To survive air raids and nuclear strikes, the underground of 404 was a labyrinth of interconnected tunnels. My parents told me that during the Sino-Soviet conflict in 1969, the Soviet Union had threatened to attack China\u2019s nuclear facilities. Back then, alarms rang frequently, sending teachers and students rushing underground.
By the time I entered school, the shelters had long been abandoned, serving only as a playground. I once tried to use an umbrella to parachute off one of the concrete blocks and ended up spraining my ankle.
It was the season when residents hung Chinese cabbage outside to dry for winter. My classmates invented a game of rock-paper-scissors nearby. The rule was simple: the loser had to grab a cabbage and throw it down into the air-raid shelter. They played all afternoon. By sunset, not a single cabbage was left in front of the building.

The abandoned primary school and the entrance to the air-raid shelter
School started at 8:30, but I would often arrive at 6:30, all by myself. I went that early precisely because no one else was there; in that solitude, I felt a quiet sense of freedom. Once, I misread the clock and arrived at 5:00 AM, only to find a little girl from the neighboring class already there. We stood at the school gate with nothing to do, so she started telling ghost stories. She told me about a room next to the slide that was locked year-round, where someone had seen a pair of bloody eyes peering out. As she spoke, she clutched her own neck and stared at me with such a sharp, intense look that I almost cried.
\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014\u2014
This was the golden age of 404\u2014a utopian bubble built on hollow ground. But bubbles, no matter how beautiful, eventually burst.
In Part 2 next week: The darkness creeps in. We\u2019ll talk about the executions in the \u201CBack Mountain,\u201D the animals in the zoo going mad, and the day the entire city began to migrate into the unknown.
Subscribe now
\",\"truncated_body_text\":\"Years later, when I saw \u201C404 Not Found\u201D on a computer screen, I was confused. How did the internet know my hometown was a secret?\",\"wordcount\":2314,\"postTags\":[{\"id\":\"927b72c2-da5f-4bae-b548-8dc9f5d5faf3\",\"publication_id\":7397205,\"name\":\"memoir\",\"slug\":\"memoir\",\"hidden\":false},{\"id\":\"a059d75b-d3ff-4892-9a92-e70c415c3c79\",\"publication_id\":7397205,\"name\":\"history\",\"slug\":\"history\",\"hidden\":false},{\"id\":\"d5548a85-82e0-4775-86d0-759fec747bf9\",\"publication_id\":7397205,\"name\":\"China\",\"slug\":\"china\",\"hidden\":false},{\"id\":\"e4ad329c-37bc-48a6-80d1-59a66a0c1a02\",\"publication_id\":7397205,\"name\":\"cold war\",\"slug\":\"cold-war\",\"hidden\":false}],\"postCountryBlocks\":[],\"headlineTest\":null,\"coverImagePalette\":{\"Vibrant\":{\"rgb\":[127.5,127.5,127.5],\"population\":0},\"DarkVibrant\":{\"rgb\":[66.3,66.3,66.3],\"population\":0},\"LightVibrant\":{\"rgb\":[188.7,188.7,188.7],\"population\":0},\"Muted\":{\"rgb\":[119,119,119],\"population\":366},\"DarkMuted\":{\"rgb\":[68,68,68],\"population\":316},\"LightMuted\":{\"rgb\":[180,180,180],\"population\":907}},\"publishedBylines\":[{\"id\":426853256,\"name\":\"Vincent\",\"handle\":\"vincent404\",\"previous_name\":\"Vincent Yan\",\"photo_url\":\"https://substack-post-media.s3.amazonaws.com/public/images/99e57cc1-8589-4ba6-825c-3bb3d1cbdbfe_1200x1200.jpeg\",\"bio\":\"I grew up in 404, a secret Chinese nuclear city that never existed on maps. Here, I write the uncensored history of life.\",\"profile_set_up_at\":\"2025-12-27T21:04:11.924Z\",\"reader_installed_at\":null,\"publicationUsers\":[{\"id\":7548366,\"user_id\":426853256,\"publication_id\":7397205,\"role\":\"admin\",\"public\":true,\"is_primary\":false,\"publication\":{\"id\":7397205,\"name\":\"Vincent\",\"subdomain\":\"vincent404\",\"custom_domain\":null,\"custom_domain_optional\":false,\"hero_text\":\"I grew up in 404, a secret Chinese nuclear city that never existed on maps. Here, I write the uncensored history of life.\",\"logo_url\":null,\"author_id\":426853256,\"primary_user_id\":426853256,\"theme_var_background_pop\":\"#FF6719\",\"created_at\":\"2025-12-27T21:26:01.229Z\",\"email_from_name\":null,\"copyright\":\"Vincent Yan\",\"founding_plan_name\":\"Founding Member\",\"community_enabled\":true,\"invite_only\":false,\"payments_state\":\"enabled\",\"language\":null,\"explicit\":false,\"homepage_type\":\"profile\",\"is_personal_mode\":true}}],\"is_guest\":false,\"bestseller_tier\":null,\"status\":{\"bestsellerTier\":null,\"subscriberTier\":null,\"leaderboard\":null,\"vip\":false,\"badge\":null,\"paidPublicationIds\":[],\"subscriber\":null}}],\"reaction\":null,\"reaction_count\":3,\"comment_count\":0,\"child_comment_count\":0,\"is_geoblocked\":false,\"hasCashtag\":false},\"publication\":{\"apple_pay_disabled\":false,\"apex_domain\":null,\"author_id\":426853256,\"byline_images_enabled\":true,\"bylines_enabled\":true,\"chartable_token\":null,\"community_enabled\":true,\"copyright\":\"Vincent Yan\",\"cover_photo_url\":null,\"created_at\":\"2025-12-27T21:26:01.229Z\",\"custom_domain_optional\":false,\"custom_domain\":null,\"default_comment_sort\":\"best_first\",\"default_coupon\":null,\"default_group_coupon\":null,\"default_show_guest_bios\":true,\"email_banner_url\":null,\"email_from_name\":null,\"email_from\":null,\"embed_tracking_disabled\":false,\"explicit\":false,\"expose_paywall_content_to_search_engines\":true,\"fb_pixel_id\":null,\"fb_site_verification_token\":null,\"flagged_as_spam\":false,\"founding_subscription_benefits\":[],\"free_subscription_benefits\":[\"Occasional public posts\"],\"ga_pixel_id\":null,\"google_site_verification_token\":null,\"google_tag_manager_token\":null,\"hero_image\":null,\"hero_text\":\"I grew up in 404, a secret Chinese nuclear city that never existed on maps. Here, I write the uncensored history of life.\",\"hide_intro_subtitle\":null,\"hide_intro_title\":null,\"hide_podcast_feed_link\":false,\"homepage_type\":\"profile\",\"id\":7397205,\"image_thumbnails_always_enabled\":false,\"invite_only\":false,\"hide_podcast_from_pub_listings\":false,\"language\":\"en\",\"logo_url_wide\":null,\"logo_url\":\"https://substackcdn.com/image/fetch/$s_!M2Je!,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F99e57cc1-8589-4ba6-825c-3bb3d1cbdbfe_1200x1200.jpeg\",\"minimum_group_size\":2,\"moderation_enabled\":true,\"name\":\"Vincent\",\"paid_subscription_benefits\":[\"Subscriber-only posts and full archive\",\"Post comments and join the community\"],\"parsely_pixel_id\":null,\"chartbeat_domain\":null,\"payments_state\":\"enabled\",\"paywall_free_trial_enabled\":true,\"podcast_art_url\":null,\"paid_podcast_episode_art_url\":null,\"podcast_byline\":null,\"podcast_description\":null,\"podcast_enabled\":false,\"podcast_feed_url\":null,\"podcast_title\":null,\"post_preview_limit\":null,\"primary_user_id\":426853256,\"require_clickthrough\":false,\"show_pub_podcast_tab\":false,\"show_recs_on_homepage\":true,\"subdomain\":\"vincent404\",\"subscriber_invites\":0,\"support_email\":null,\"theme_var_background_pop\":\"#FF6719\",\"theme_var_color_links\":false,\"theme_var_cover_bg_color\":null,\"trial_end_override\":null,\"twitter_pixel_id\":null,\"type\":\"newsletter\",\"post_reaction_faces_enabled\":true,\"is_personal_mode\":true,\"plans\":[{\"id\":\"yearly50usd\",\"object\":\"plan\",\"active\":true,\"aggregate_usage\":null,\"amount\":5000,\"amount_decimal\":\"5000\",\"billing_scheme\":\"per_unit\",\"created\":1766908640,\"currency\":\"usd\",\"interval\":\"year\",\"interval_count\":1,\"livemode\":true,\"metadata\":{\"substack\":\"yes\"},\"meter\":null,\"nickname\":\"$50 a year\",\"product\":\"prod_Tgc54cTk8kEkaz\",\"tiers\":null,\"tiers_mode\":null,\"transform_usage\":null,\"trial_period_days\":null,\"usage_type\":\"licensed\",\"currency_options\":{\"aud\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":7500,\"unit_amount_decimal\":\"7500\"},\"brl\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":28000,\"unit_amount_decimal\":\"28000\"},\"cad\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":7000,\"unit_amount_decimal\":\"7000\"},\"chf\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":4000,\"unit_amount_decimal\":\"4000\"},\"dkk\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":32000,\"unit_amount_decimal\":\"32000\"},\"eur\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":4300,\"unit_amount_decimal\":\"4300\"},\"gbp\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":3800,\"unit_amount_decimal\":\"3800\"},\"mxn\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":90000,\"unit_amount_decimal\":\"90000\"},\"nok\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":50500,\"unit_amount_decimal\":\"50500\"},\"nzd\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":9000,\"unit_amount_decimal\":\"9000\"},\"pln\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":18000,\"unit_amount_decimal\":\"18000\"},\"sek\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":46000,\"unit_amount_decimal\":\"46000\"},\"usd\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":5000,\"unit_amount_decimal\":\"5000\"}}},{\"id\":\"monthly5usd\",\"object\":\"plan\",\"active\":true,\"aggregate_usage\":null,\"amount\":500,\"amount_decimal\":\"500\",\"billing_scheme\":\"per_unit\",\"created\":1766908640,\"currency\":\"usd\",\"interval\":\"month\",\"interval_count\":1,\"livemode\":true,\"metadata\":{\"substack\":\"yes\"},\"meter\":null,\"nickname\":\"$5 a month\",\"product\":\"prod_Tgc5LE1Wp8fWjc\",\"tiers\":null,\"tiers_mode\":null,\"transform_usage\":null,\"trial_period_days\":null,\"usage_type\":\"licensed\",\"currency_options\":{\"aud\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":800,\"unit_amount_decimal\":\"800\"},\"brl\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":2800,\"unit_amount_decimal\":\"2800\"},\"cad\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":700,\"unit_amount_decimal\":\"700\"},\"chf\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":400,\"unit_amount_decimal\":\"400\"},\"dkk\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":3200,\"unit_amount_decimal\":\"3200\"},\"eur\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":500,\"unit_amount_decimal\":\"500\"},\"gbp\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":400,\"unit_amount_decimal\":\"400\"},\"mxn\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":9000,\"unit_amount_decimal\":\"9000\"},\"nok\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":5500,\"unit_amount_decimal\":\"5500\"},\"nzd\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":900,\"unit_amount_decimal\":\"900\"},\"pln\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":1800,\"unit_amount_decimal\":\"1800\"},\"sek\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":4600,\"unit_amount_decimal\":\"4600\"},\"usd\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":500,\"unit_amount_decimal\":\"500\"}}},{\"id\":\"founding10000usd\",\"name\":\"founding10000usd\",\"nickname\":\"founding10000usd\",\"active\":true,\"amount\":10000,\"currency\":\"usd\",\"interval\":\"year\",\"interval_count\":1,\"metadata\":{\"substack\":\"yes\",\"founding\":\"yes\",\"no_coupons\":\"yes\",\"short_description\":\"Founding Member\",\"short_description_english\":\"Founding Member\",\"minimum\":\"10000\",\"minimum_local\":{\"aud\":15000,\"brl\":55500,\"cad\":14000,\"chf\":8000,\"dkk\":63500,\"eur\":8500,\"gbp\":7500,\"mxn\":179500,\"nok\":100500,\"nzd\":17500,\"pln\":36000,\"sek\":92000,\"usd\":10000}},\"currency_options\":{\"aud\":{\"unit_amount\":15000,\"tax_behavior\":\"unspecified\"},\"brl\":{\"unit_amount\":55500,\"tax_behavior\":\"unspecified\"},\"cad\":{\"unit_amount\":14000,\"tax_behavior\":\"unspecified\"},\"chf\":{\"unit_amount\":8000,\"tax_behavior\":\"unspecified\"},\"dkk\":{\"unit_amount\":63500,\"tax_behavior\":\"unspecified\"},\"eur\":{\"unit_amount\":8500,\"tax_behavior\":\"unspecified\"},\"gbp\":{\"unit_amount\":7500,\"tax_behavior\":\"unspecified\"},\"mxn\":{\"unit_amount\":179500,\"tax_behavior\":\"unspecified\"},\"nok\":{\"unit_amount\":100500,\"tax_behavior\":\"unspecified\"},\"nzd\":{\"unit_amount\":17500,\"tax_behavior\":\"unspecified\"},\"pln\":{\"unit_amount\":36000,\"tax_behavior\":\"unspecified\"},\"sek\":{\"unit_amount\":92000,\"tax_behavior\":\"unspecified\"},\"usd\":{\"unit_amount\":10000,\"tax_behavior\":\"unspecified\"}}}],\"stripe_user_id\":\"acct_1SjERKGXUjXKSpKk\",\"stripe_country\":\"CA\",\"stripe_publishable_key\":\"pk_live_51SjERKGXUjXKSpKkVZoafIp7AUb7jMelcfR1YuASJFLBulFRch90LcBMtpvN3uFKyP0KPejQUzhxN1RRA1OC0Ehq003Dtd0Dye\",\"stripe_platform_account\":\"US\",\"automatic_tax_enabled\":false,\"author_name\":\"Vincent\",\"author_handle\":\"vincent404\",\"author_photo_url\":\"https://substackcdn.com/image/fetch/$s_!M2Je!,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F99e57cc1-8589-4ba6-825c-3bb3d1cbdbfe_1200x1200.jpeg\",\"author_bio\":\"I grew up in 404, a secret Chinese nuclear city that never existed on maps. Here, I write the uncensored history of life.\",\"has_custom_tos\":false,\"has_custom_privacy\":false,\"theme\":{\"background_pop_color\":null,\"web_bg_color\":null,\"cover_bg_color\":null,\"home_hero\":\"newspaper\",\"home_posts\":\"list\"},\"threads_v2_settings\":{\"photo_replies_enabled\":true,\"first_thread_email_sent_at\":null,\"create_thread_minimum_role\":\"contributor\",\"activated_at\":null,\"reader_thread_notifications_enabled\":true,\"boost_free_subscriber_chat_preview_enabled\":true,\"push_suppression_enabled\":false},\"default_group_coupon_percent_off\":null,\"pause_return_date\":null,\"has_posts\":false,\"has_recommendations\":false,\"first_post_date\":\"2025-12-28T03:41:34.654Z\",\"has_podcast\":false,\"has_free_podcast\":false,\"has_subscriber_only_podcast\":false,\"has_community_content\":false,\"rankingDetail\":\"Launched 7 hours ago\",\"rankingDetailFreeIncluded\":\"Launched 7 hours ago\",\"rankingDetailOrderOfMagnitude\":0,\"rankingDetailFreeIncludedOrderOfMagnitude\":1,\"rankingDetailFreeSubscriberCount\":null,\"rankingDetailByLanguage\":{\"de\":{\"rankingDetail\":\"Vor vor 7 Stunden gelauncht\",\"rankingDetailFreeIncluded\":\"Vor vor 7 Stunden gelauncht\",\"rankingDetailOrderOfMagnitude\":0,\"rankingDetailFreeIncludedOrderOfMagnitude\":1,\"rankingDetailFreeSubscriberCount\":null,\"freeSubscriberCount\":null,\"freeSubscriberCountOrderOfMagnitude\":\"1\"},\"es\":{\"rankingDetail\":\"Lanzado hace 7 horas\",\"rankingDetailFreeIncluded\":\"Lanzado hace 7 horas\",\"rankingDetailOrderOfMagnitude\":0,\"rankingDetailFreeIncludedOrderOfMagnitude\":1,\"rankingDetailFreeSubscriberCount\":null,\"freeSubscriberCount\":null,\"freeSubscriberCountOrderOfMagnitude\":\"1\"},\"fr\":{\"rankingDetail\":\"Lanc\u00E9 il y a 7 heures\",\"rankingDetailFreeIncluded\":\"Lanc\u00E9 il y a 7 heures\",\"rankingDetailOrderOfMagnitude\":0,\"rankingDetailFreeIncludedOrderOfMagnitude\":1,\"rankingDetailFreeSubscriberCount\":null,\"freeSubscriberCount\":null,\"freeSubscriberCountOrderOfMagnitude\":\"1\"},\"pt\":{\"rankingDetail\":\"Lan\u00E7ado 7 horas\",\"rankingDetailFreeIncluded\":\"Lan\u00E7ado 7 horas\",\"rankingDetailOrderOfMagnitude\":0,\"rankingDetailFreeIncludedOrderOfMagnitude\":1,\"rankingDetailFreeSubscriberCount\":null,\"freeSubscriberCount\":null,\"freeSubscriberCountOrderOfMagnitude\":\"1\"},\"pt-br\":{\"rankingDetail\":\"Lan\u00E7ado 7 horas\",\"rankingDetailFreeIncluded\":\"Lan\u00E7ado 7 horas\",\"rankingDetailOrderOfMagnitude\":0,\"rankingDetailFreeIncludedOrderOfMagnitude\":1,\"rankingDetailFreeSubscriberCount\":null,\"freeSubscriberCount\":null,\"freeSubscriberCountOrderOfMagnitude\":\"1\"},\"it\":{\"rankingDetail\":\"Lanciato 7 ore\",\"rankingDetailFreeIncluded\":\"Lanciato 7 ore\",\"rankingDetailOrderOfMagnitude\":0,\"rankingDetailFreeIncludedOrderOfMagnitude\":1,\"rankingDetailFreeSubscriberCount\":null,\"freeSubscriberCount\":null,\"freeSubscriberCountOrderOfMagnitude\":\"1\"},\"en\":{\"rankingDetail\":\"Launched 7 hours ago\",\"rankingDetailFreeIncluded\":\"Launched 7 hours ago\",\"rankingDetailOrderOfMagnitude\":0,\"rankingDetailFreeIncludedOrderOfMagnitude\":1,\"rankingDetailFreeSubscriberCount\":null,\"freeSubscriberCount\":null,\"freeSubscriberCountOrderOfMagnitude\":\"1\"}},\"freeSubscriberCount\":null,\"freeSubscriberCountOrderOfMagnitude\":\"1\",\"author_bestseller_tier\":0,\"author_badge\":null,\"disable_monthly_subscriptions\":false,\"disable_annual_subscriptions\":false,\"hide_post_restacks\":false,\"notes_feed_enabled\":true,\"showIntroModule\":false,\"isPortraitLayout\":false,\"last_chat_post_at\":null,\"leaderboard_ranking\":null,\"primary_profile_name\":\"Vincent\",\"primary_profile_photo_url\":\"https://substackcdn.com/image/fetch/$s_!M2Je!,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F99e57cc1-8589-4ba6-825c-3bb3d1cbdbfe_1200x1200.jpeg\",\"no_follow\":true,\"paywall_chat\":\"free\",\"sections\":[],\"multipub_migration\":null,\"navigationBarItems\":[],\"contributors\":[{\"name\":\"Vincent Yan\",\"handle\":\"vincent404\",\"role\":\"admin\",\"owner\":true,\"user_id\":426853256,\"photo_url\":\"https://substack-post-media.s3.amazonaws.com/public/images/64f05071-02c1-4d7b-84fa-f94830be5e9d_144x144.png\",\"bio\":\"I grew up in 404, a secret Chinese nuclear city that never existed on maps. Here, I write the uncensored history of life.\"}],\"threads_v2_enabled\":true,\"viralGiftsConfig\":{\"id\":\"5be31936-dd72-4451-8320-2550b333306b\",\"publication_id\":7397205,\"enabled\":true,\"gifts_per_user\":5,\"gift_length_months\":1,\"send_extra_gifts\":true,\"message\":\"I grew up in 404, a secret Chinese nuclear city that never existed on maps. Here, I write the uncensored history of life.\",\"created_at\":\"2025-12-28T07:57:24.774328+00:00\",\"updated_at\":\"2025-12-28T07:57:24.774328+00:00\",\"days_til_invite\":14,\"send_emails\":true,\"show_link\":null,\"grant_email_body\":null,\"grant_email_subject\":null},\"tier\":0,\"no_index\":true,\"can_set_google_site_verification\":false,\"can_have_sitemap\":false,\"draft_iap_advanced_plans\":[{\"sku\":\"Cm7soSc4u0ZCsTJ0Ke\",\"publication_id\":\"7397205\",\"is_active\":true,\"price_base_units\":700,\"currency_alpha3\":\"usd\",\"period\":\"month\",\"created_at\":\"2025-12-28T07:57:22.056Z\",\"updated_at\":\"2025-12-28T07:57:22.056Z\",\"id\":\"829635\",\"payout_amount_base_units\":50,\"alternate_currencies\":{\"aud\":1100,\"brl\":3900,\"cad\":1000,\"chf\":600,\"dkk\":4500,\"eur\":600,\"gbp\":600,\"mxn\":13000,\"nok\":7500,\"nzd\":1200,\"pln\":2600,\"sek\":6500},\"display_name\":\"Vincent (Monthly)\",\"display_price\":\"$7\"},{\"sku\":\"9vTNjkKBUGij1KnreL\",\"publication_id\":\"7397205\",\"is_active\":true,\"price_base_units\":7000,\"currency_alpha3\":\"usd\",\"period\":\"year\",\"created_at\":\"2025-12-28T07:57:22.071Z\",\"updated_at\":\"2025-12-28T07:57:22.071Z\",\"id\":\"829636\",\"payout_amount_base_units\":500,\"alternate_currencies\":{\"aud\":10500,\"brl\":39000,\"cad\":10000,\"chf\":6000,\"dkk\":44500,\"eur\":6000,\"gbp\":5500,\"mxn\":125500,\"nok\":70500,\"nzd\":12000,\"pln\":25500,\"sek\":64500},\"display_name\":\"Vincent (Yearly)\",\"display_price\":\"$70\"}],\"iap_advanced_plans\":[{\"sku\":\"Cm7soSc4u0ZCsTJ0Ke\",\"publication_id\":\"7397205\",\"is_active\":true,\"price_base_units\":700,\"currency_alpha3\":\"usd\",\"period\":\"month\",\"created_at\":\"2025-12-28T07:57:22.056Z\",\"updated_at\":\"2025-12-28T07:57:22.056Z\",\"id\":\"829635\",\"payout_amount_base_units\":50,\"alternate_currencies\":{\"aud\":1100,\"brl\":3900,\"cad\":1000,\"chf\":600,\"dkk\":4500,\"eur\":600,\"gbp\":600,\"mxn\":13000,\"nok\":7500,\"nzd\":1200,\"pln\":2600,\"sek\":6500},\"display_name\":\"Vincent (Monthly)\",\"display_price\":\"$7\"},{\"sku\":\"9vTNjkKBUGij1KnreL\",\"publication_id\":\"7397205\",\"is_active\":true,\"price_base_units\":7000,\"currency_alpha3\":\"usd\",\"period\":\"year\",\"created_at\":\"2025-12-28T07:57:22.071Z\",\"updated_at\":\"2025-12-28T07:57:22.071Z\",\"id\":\"829636\",\"payout_amount_base_units\":500,\"alternate_currencies\":{\"aud\":10500,\"brl\":39000,\"cad\":10000,\"chf\":6000,\"dkk\":44500,\"eur\":6000,\"gbp\":5500,\"mxn\":125500,\"nok\":70500,\"nzd\":12000,\"pln\":25500,\"sek\":64500},\"display_name\":\"Vincent (Yearly)\",\"display_price\":\"$70\"}],\"founding_plan_name_english\":\"Founding Member\",\"draft_plans\":[{\"id\":\"yearly50usd\",\"object\":\"plan\",\"active\":true,\"aggregate_usage\":null,\"amount\":5000,\"amount_decimal\":\"5000\",\"billing_scheme\":\"per_unit\",\"created\":1766908640,\"currency\":\"usd\",\"interval\":\"year\",\"interval_count\":1,\"livemode\":true,\"metadata\":{\"substack\":\"yes\"},\"meter\":null,\"nickname\":\"$50 a year\",\"product\":\"prod_Tgc54cTk8kEkaz\",\"tiers\":null,\"tiers_mode\":null,\"transform_usage\":null,\"trial_period_days\":null,\"usage_type\":\"licensed\",\"currency_options\":{\"aud\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":7500,\"unit_amount_decimal\":\"7500\"},\"brl\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":28000,\"unit_amount_decimal\":\"28000\"},\"cad\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":7000,\"unit_amount_decimal\":\"7000\"},\"chf\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":4000,\"unit_amount_decimal\":\"4000\"},\"dkk\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":32000,\"unit_amount_decimal\":\"32000\"},\"eur\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":4300,\"unit_amount_decimal\":\"4300\"},\"gbp\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":3800,\"unit_amount_decimal\":\"3800\"},\"mxn\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":90000,\"unit_amount_decimal\":\"90000\"},\"nok\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":50500,\"unit_amount_decimal\":\"50500\"},\"nzd\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":9000,\"unit_amount_decimal\":\"9000\"},\"pln\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":18000,\"unit_amount_decimal\":\"18000\"},\"sek\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":46000,\"unit_amount_decimal\":\"46000\"},\"usd\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":5000,\"unit_amount_decimal\":\"5000\"}}},{\"id\":\"monthly5usd\",\"object\":\"plan\",\"active\":true,\"aggregate_usage\":null,\"amount\":500,\"amount_decimal\":\"500\",\"billing_scheme\":\"per_unit\",\"created\":1766908640,\"currency\":\"usd\",\"interval\":\"month\",\"interval_count\":1,\"livemode\":true,\"metadata\":{\"substack\":\"yes\"},\"meter\":null,\"nickname\":\"$5 a month\",\"product\":\"prod_Tgc5LE1Wp8fWjc\",\"tiers\":null,\"tiers_mode\":null,\"transform_usage\":null,\"trial_period_days\":null,\"usage_type\":\"licensed\",\"currency_options\":{\"aud\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":800,\"unit_amount_decimal\":\"800\"},\"brl\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":2800,\"unit_amount_decimal\":\"2800\"},\"cad\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":700,\"unit_amount_decimal\":\"700\"},\"chf\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":400,\"unit_amount_decimal\":\"400\"},\"dkk\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":3200,\"unit_amount_decimal\":\"3200\"},\"eur\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":500,\"unit_amount_decimal\":\"500\"},\"gbp\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":400,\"unit_amount_decimal\":\"400\"},\"mxn\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":9000,\"unit_amount_decimal\":\"9000\"},\"nok\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":5500,\"unit_amount_decimal\":\"5500\"},\"nzd\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":900,\"unit_amount_decimal\":\"900\"},\"pln\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":1800,\"unit_amount_decimal\":\"1800\"},\"sek\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":4600,\"unit_amount_decimal\":\"4600\"},\"usd\":{\"custom_unit_amount\":null,\"tax_behavior\":\"unspecified\",\"unit_amount\":500,\"unit_amount_decimal\":\"500\"}}},{\"id\":\"founding10000usd\",\"name\":\"founding10000usd\",\"nickname\":\"founding10000usd\",\"active\":true,\"amount\":10000,\"currency\":\"usd\",\"interval\":\"year\",\"interval_count\":1,\"metadata\":{\"substack\":\"yes\",\"founding\":\"yes\",\"no_coupons\":\"yes\",\"short_description\":\"Founding Member\",\"short_description_english\":\"Founding Member\",\"minimum\":\"10000\",\"minimum_local\":{\"aud\":15000,\"brl\":55500,\"cad\":14000,\"chf\":8000,\"dkk\":63500,\"eur\":8500,\"gbp\":7500,\"mxn\":179500,\"nok\":100500,\"nzd\":17500,\"pln\":36000,\"sek\":92000,\"usd\":10000}},\"currency_options\":{\"aud\":{\"unit_amount\":15000,\"tax_behavior\":\"unspecified\"},\"brl\":{\"unit_amount\":55500,\"tax_behavior\":\"unspecified\"},\"cad\":{\"unit_amount\":14000,\"tax_behavior\":\"unspecified\"},\"chf\":{\"unit_amount\":8000,\"tax_behavior\":\"unspecified\"},\"dkk\":{\"unit_amount\":63500,\"tax_behavior\":\"unspecified\"},\"eur\":{\"unit_amount\":8500,\"tax_behavior\":\"unspecified\"},\"gbp\":{\"unit_amount\":7500,\"tax_behavior\":\"unspecified\"},\"mxn\":{\"unit_amount\":179500,\"tax_behavior\":\"unspecified\"},\"nok\":{\"unit_amount\":100500,\"tax_behavior\":\"unspecified\"},\"nzd\":{\"unit_amount\":17500,\"tax_behavior\":\"unspecified\"},\"pln\":{\"unit_amount\":36000,\"tax_behavior\":\"unspecified\"},\"sek\":{\"unit_amount\":92000,\"tax_behavior\":\"unspecified\"},\"usd\":{\"unit_amount\":10000,\"tax_behavior\":\"unspecified\"}}}],\"paid_subscription_benefits_english\":[\"Subscriber-only posts and full archive\",\"Post comments and join the community\"],\"free_subscription_benefits_english\":[\"Occasional public posts\"],\"bundles\":[],\"base_url\":\"https://vincent404.substack.com\",\"hostname\":\"vincent404.substack.com\",\"is_on_substack\":false,\"spotify_podcast_settings\":null,\"podcastPalette\":{\"DarkMuted\":{\"population\":72,\"rgb\":[73,153,137]},\"DarkVibrant\":{\"population\":6013,\"rgb\":[4,100,84]},\"LightMuted\":{\"population\":7,\"rgb\":[142,198,186]},\"LightVibrant\":{\"population\":3,\"rgb\":[166,214,206]},\"Muted\":{\"population\":6,\"rgb\":[92,164,156]},\"Vibrant\":{\"population\":5,\"rgb\":[76,164,146]}},\"pageThemes\":{\"podcast\":null},\"appTheme\":{\"colors\":{\"accent\":{\"name\":\"#ff6719\",\"primary\":{\"r\":255,\"g\":103,\"b\":25,\"a\":1},\"primary_hover\":{\"r\":232,\"g\":83,\"b\":0,\"a\":1},\"primary_elevated\":{\"r\":232,\"g\":83,\"b\":0,\"a\":1},\"secondary\":{\"r\":255,\"g\":103,\"b\":25,\"a\":0.2},\"contrast\":{\"r\":255,\"g\":255,\"b\":255,\"a\":1},\"bg\":{\"r\":255,\"g\":103,\"b\":25,\"a\":0.2},\"bg_hover\":{\"r\":255,\"g\":103,\"b\":25,\"a\":0.3},\"dark\":{\"primary\":{\"r\":255,\"g\":103,\"b\":25,\"a\":1},\"primary_hover\":{\"r\":255,\"g\":132,\"b\":73,\"a\":1},\"primary_elevated\":{\"r\":255,\"g\":132,\"b\":73,\"a\":1},\"secondary\":{\"r\":255,\"g\":103,\"b\":25,\"a\":0.2},\"contrast\":{\"r\":255,\"g\":255,\"b\":255,\"a\":1},\"bg\":{\"r\":255,\"g\":103,\"b\":25,\"a\":0.2},\"bg_hover\":{\"r\":255,\"g\":103,\"b\":25,\"a\":0.3}}},\"fg\":{\"primary\":{\"r\":0,\"g\":0,\"b\":0,\"a\":0.8},\"secondary\":{\"r\":0,\"g\":0,\"b\":0,\"a\":0.6},\"tertiary\":{\"r\":0,\"g\":0,\"b\":0,\"a\":0.4},\"accent\":{\"r\":213,\"g\":66,\"b\":0,\"a\":1},\"dark\":{\"primary\":{\"r\":255,\"g\":255,\"b\":255,\"a\":0.9},\"secondary\":{\"r\":255,\"g\":255,\"b\":255,\"a\":0.6},\"tertiary\":{\"r\":255,\"g\":255,\"b\":255,\"a\":0.4},\"accent\":{\"r\":255,\"g\":103,\"b\":25,\"a\":1}}},\"bg\":{\"name\":\"#ffffff\",\"hue\":{\"r\":255,\"g\":255,\"b\":255,\"a\":0},\"tint\":{\"r\":255,\"g\":255,\"b\":255,\"a\":0},\"primary\":{\"r\":255,\"g\":255,\"b\":255,\"a\":1},\"primary_hover\":{\"r\":250,\"g\":250,\"b\":250,\"a\":1},\"primary_elevated\":{\"r\":250,\"g\":250,\"b\":250,\"a\":1},\"secondary\":{\"r\":238,\"g\":238,\"b\":238,\"a\":1},\"secondary_elevated\":{\"r\":206.90096477355226,\"g\":206.90096477355175,\"b\":206.9009647735519,\"a\":1},\"tertiary\":{\"r\":219,\"g\":219,\"b\":219,\"a\":1},\"quaternary\":{\"r\":182,\"g\":182,\"b\":182,\"a\":1},\"dark\":{\"primary\":{\"r\":22,\"g\":23,\"b\":24,\"a\":1},\"primary_hover\":{\"r\":27,\"g\":28,\"b\":29,\"a\":1},\"primary_elevated\":{\"r\":27,\"g\":28,\"b\":29,\"a\":1},\"secondary\":{\"r\":35,\"g\":37,\"b\":37,\"a\":1},\"secondary_elevated\":{\"r\":41.35899397549579,\"g\":43.405356429195315,\"b\":43.40489285041963,\"a\":1},\"tertiary\":{\"r\":54,\"g\":55,\"b\":55,\"a\":1},\"quaternary\":{\"r\":90,\"g\":91,\"b\":91,\"a\":1}}}}},\"live_subscriber_counts\":true,\"supports_ip_content_unlock\":false,\"logoPalette\":{\"Vibrant\":{\"rgb\":[127.5,127.5,127.5],\"population\":0},\"DarkVibrant\":{\"rgb\":[66.3,66.3,66.3],\"population\":0},\"LightVibrant\":{\"rgb\":[188.7,188.7,188.7],\"population\":0},\"Muted\":{\"rgb\":[132,132,131],\"population\":252},\"DarkMuted\":{\"rgb\":[68,68,66],\"population\":193},\"LightMuted\":{\"rgb\":[192,192,192],\"population\":384}}},\"publicationSettings\":{\"block_ai_crawlers\":false,\"credit_token_enabled\":true,\"custom_tos_and_privacy\":false,\"did_identity\":null,\"disable_optimistic_bank_payments\":false,\"display_welcome_page_details\":true,\"enable_meetings\":false,\"payment_pledges_enabled\":true,\"enable_post_page_conversion\":true,\"enable_prev_next_nav\":false,\"enable_restacking\":true,\"gifts_from_substack_disabled\":false,\"google_analytics_4_token\":null,\"group_sections_and_podcasts_in_menu_enabled\":false,\"live_stream_homepage_visibility\":\"contributorsAndAdmins\",\"live_stream_homepage_style\":\"autoPlay\",\"medium_length_description\":\"\",\"notes_feed_enabled\":true,\"paywall_unlock_tokens\":true,\"post_preview_crop_gravity\":\"auto\",\"reader_referrals_enabled\":false,\"reader_referrals_leaderboard_enabled\":false,\"seen_coming_soon_explainer\":false,\"seen_google_analytics_migration_modal\":false,\"local_currency_modal_seen\":true,\"local_payment_methods_modal_seen\":false,\"twitter_pixel_signup_event_id\":null,\"twitter_pixel_subscribe_event_id\":null,\"use_local_currency\":true,\"welcome_page_opt_out_text\":\"No thanks\",\"cookie_settings\":\"\",\"show_restacks_below_posts\":true,\"holiday_gifting_post_header\":true,\"homepage_message_text\":\"\",\"homepage_message_link\":\"\",\"about_us_author_ids\":\"\",\"archived_section_ids\":\"\",\"column_section_ids\":\"\",\"fp_primary_column_section_ids\":\"\",\"event_section_ids\":\"\",\"podcasts_metadata\":\"\",\"video_section_ids\":\"\",\"post_metering_enabled\":false}}},\"profile\":null,\"hideHeader\":true,\"hideFooter\":true,\"useManifest\":true,\"useWebapp\":true,\"useDarkMode\":true,\"autoTriggerSignin\":false,\"noIndex\":false,\"isEligibleForLiveStreamCreation\":false,\"scheduledLiveStreams\":[],\"features\":{},\"browser\":{\"name\":\"Chrome\",\"version\":\"69.0.3497.100\",\"major\":\"69\"},\"showCookieBanner\":true,\"disabledCookies\":[\"intro_popup_last_hidden_at\",\"muxData-substack\",\"like_upsell_last_shown_at\",\"chatbot_terms_last_accepted_at\",\"preferred_language\",\"visit_id\",\"ajs_anonymous_id\",\"ab_testing_id\",\"ab_experiment_sampled\",\"_ga_tracking-substack\",\"ad_quick_tracking_pixel-substack\",\"meta_tracking_pixel-substack\",\"_dd_s-substack\",\"fs_uid-substack\",\"__zlcmid-substack\",\"disable_html_pixels\"],\"dd_env\":\"prod\",\"dd_ti\":false}")
This site requires JavaScript to run correctly. Please turn on JavaScript or unblock scripts
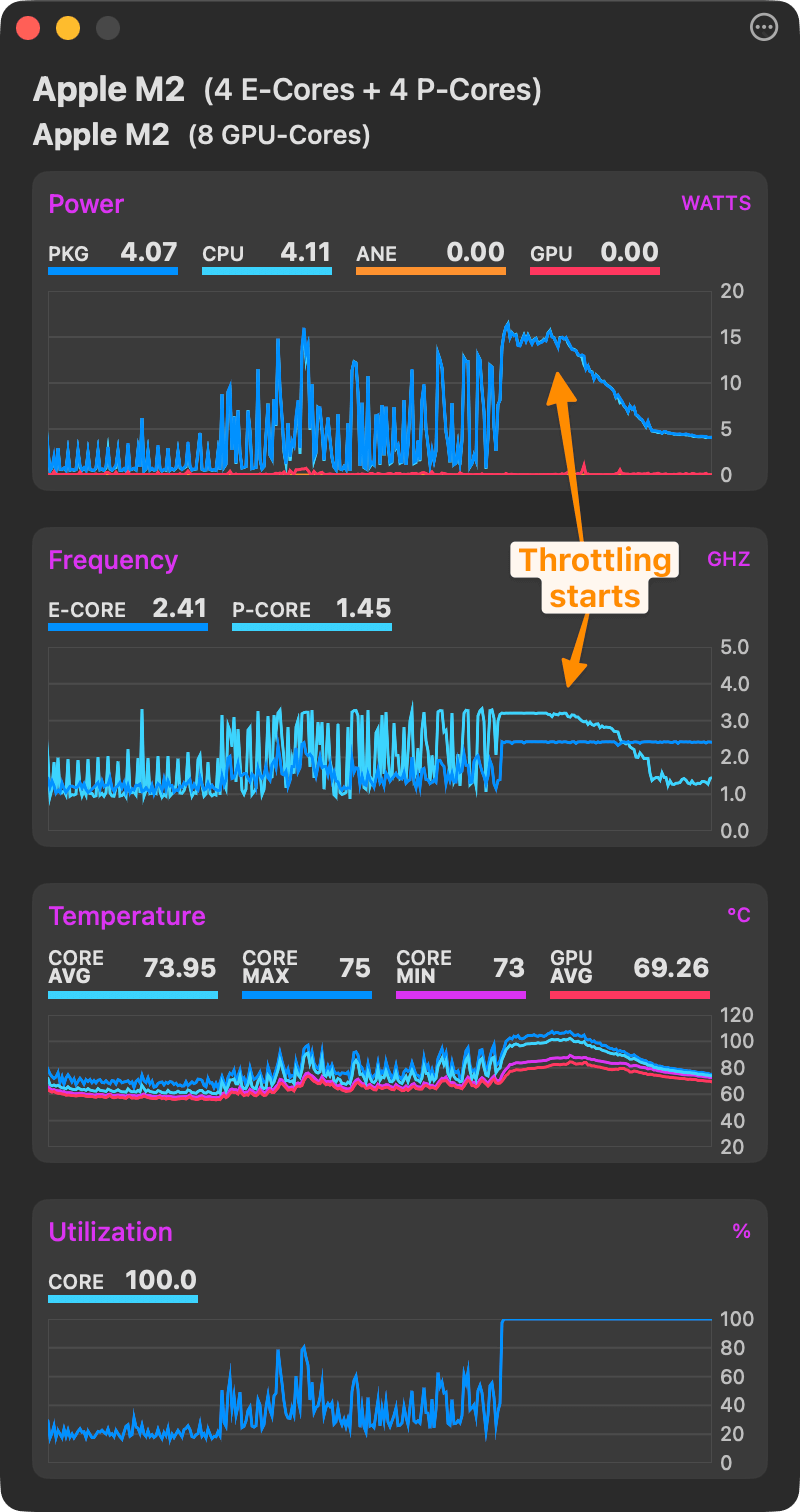
 An early version of MacThrottle, just reporthing the thermal state
An early version of MacThrottle, just reporthing the thermal state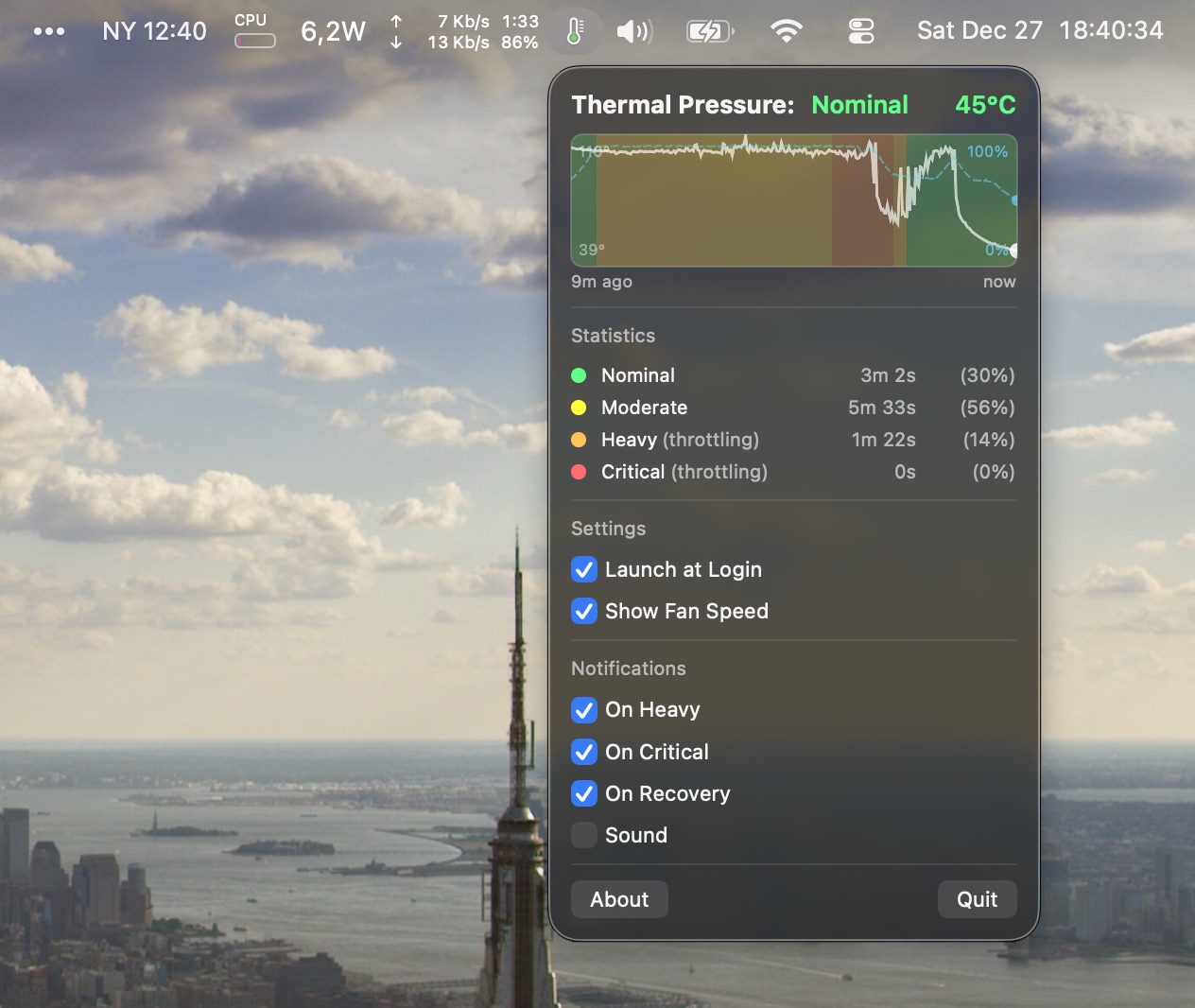 Graph with pressure state, temp and fans. Tooltip on hover to get past value is supported.
Graph with pressure state, temp and fans. Tooltip on hover to get past value is supported.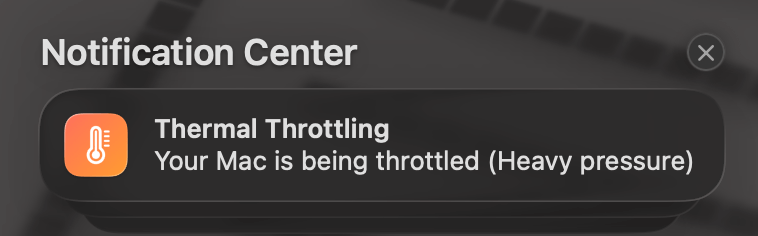 To be fair, it can get a bit noisy on a struggling Macbook Air…
To be fair, it can get a bit noisy on a struggling Macbook Air…



















 When Mickey Mouse 1.0 went into the public domain in 2024, he joined a host of other public domain characters—Winnie-the-Pooh, Sherlock Holmes, Snow White, Cinderella, Dracula, Frankenstein's Monster, Robin Hood, Santa Claus, and the Wonderful Wizard of Oz characters, to name a few. This year, we get the first versions of Betty Boop and Pluto (originally named Rover) and new iterations of Mickey and Minnie Mouse. Looking ahead, an exciting new cast of characters will become public domain in the coming years: the initial appearance of Goofy in 2028 (originally named Dippy Dawg), Donald Duck in 2030, Superman in 2034, Batman in 2035, Tom and Jerry and Bugs Bunny in 2036, and Wonder Woman in 2037.
When Mickey Mouse 1.0 went into the public domain in 2024, he joined a host of other public domain characters—Winnie-the-Pooh, Sherlock Holmes, Snow White, Cinderella, Dracula, Frankenstein's Monster, Robin Hood, Santa Claus, and the Wonderful Wizard of Oz characters, to name a few. This year, we get the first versions of Betty Boop and Pluto (originally named Rover) and new iterations of Mickey and Minnie Mouse. Looking ahead, an exciting new cast of characters will become public domain in the coming years: the initial appearance of Goofy in 2028 (originally named Dippy Dawg), Donald Duck in 2030, Superman in 2034, Batman in 2035, Tom and Jerry and Bugs Bunny in 2036, and Wonder Woman in 2037. 
 Here is how this nuance plays out in one Mickey story without a renewed copyright—the 1934 tale of Rumplewatt the Giant. This story introduces a gnome village from which the titular giant steals a golden goose. After Mickey defeats the giant, the butterfly who initially flew him to the castle morphs into Princess Minnie. As a reward for his valiance, she agrees to marry Mickey. So far as we can tell, these elements were newly introduced in the 1934 comic. If this is correct, they are in the public domain due to non-renewal.
Here is how this nuance plays out in one Mickey story without a renewed copyright—the 1934 tale of Rumplewatt the Giant. This story introduces a gnome village from which the titular giant steals a golden goose. After Mickey defeats the giant, the butterfly who initially flew him to the castle morphs into Princess Minnie. As a reward for his valiance, she agrees to marry Mickey. So far as we can tell, these elements were newly introduced in the 1934 comic. If this is correct, they are in the public domain due to non-renewal. At the same time, Rumplewatt the Giant derived many of its elements from the still-copyrighted cartoon Giantland (1933). These include a sequence where Mickey hides in a sugar-cube jar and ends up in the giant’s coffee cup, and a bit where Mickey uses pepper to make the giant sneeze. Assuming these were original to Giantland, they are still copyrighted. Even though they reappear in the non-renewed comic, they are not in the public domain because they originated in a work that is still under copyright. Finally, both works share basic “ideas” that are uncopyrightable and were always in the public domain—these include the generic “hero fights a giant and defeats him” plot line.
At the same time, Rumplewatt the Giant derived many of its elements from the still-copyrighted cartoon Giantland (1933). These include a sequence where Mickey hides in a sugar-cube jar and ends up in the giant’s coffee cup, and a bit where Mickey uses pepper to make the giant sneeze. Assuming these were original to Giantland, they are still copyrighted. Even though they reappear in the non-renewed comic, they are not in the public domain because they originated in a work that is still under copyright. Finally, both works share basic “ideas” that are uncopyrightable and were always in the public domain—these include the generic “hero fights a giant and defeats him” plot line.
 This is interesting because while Fleischer Studios does own continuing trademark rights over Betty Boop (discussed below), its claim to copyright over the fully developed character is less clear. In fact, in 2011, an appeals court definitively
This is interesting because while Fleischer Studios does own continuing trademark rights over Betty Boop (discussed below), its claim to copyright over the fully developed character is less clear. In fact, in 2011, an appeals court definitively 
 That Betty Boop is in the public domain, along with the lyrics, plot, and incredible animation. So are the Boops from other 1930 cartoons (to the left, Barnacle Bill and Mysterious Mose). However, those are not the only parts of the character in the public domain. Some of her features were not copyrightable from the beginning, because they were copied from elsewhere. Her general appearance and “Boop Oop A Doop” catchphrase were inspired by the Jazz Age flapper girl archetype, as embodied by celebrities such as Helen Kane.
That Betty Boop is in the public domain, along with the lyrics, plot, and incredible animation. So are the Boops from other 1930 cartoons (to the left, Barnacle Bill and Mysterious Mose). However, those are not the only parts of the character in the public domain. Some of her features were not copyrightable from the beginning, because they were copied from elsewhere. Her general appearance and “Boop Oop A Doop” catchphrase were inspired by the Jazz Age flapper girl archetype, as embodied by celebrities such as Helen Kane.
 Fleischer owns trademark rights to the words “Betty Boop” and “Boop” for products such as live musical theater performances and clothing. It also has trademarks over Betty Boop designs such as the one depicted here for a range of merchandise including jewelry, wallets, back packs, drinking glasses, plastic water bottles, clothing, and dolls. (As noted by the Ninth Circuit appeals court in the case rejecting Fleischer’s copyright claim, it turns out that Boop merchandise is extremely popular, even appearing in the most surprising locations: “This merchandise has reached such a high level of popularity that even drug dealers have been known to use it. See United States v. Lakoskey, 462 F.3d 965, 971 (8th Cir. 2006) (‘A search warrant was issued, and the package was opened pursuant to that warrant on January 26, 2004. The package contained a large ceramic Betty Boop doll, with four concealed, separately wrapped plastic bundles of high-purity-level methamphetamine inside’).”)
Fleischer owns trademark rights to the words “Betty Boop” and “Boop” for products such as live musical theater performances and clothing. It also has trademarks over Betty Boop designs such as the one depicted here for a range of merchandise including jewelry, wallets, back packs, drinking glasses, plastic water bottles, clothing, and dolls. (As noted by the Ninth Circuit appeals court in the case rejecting Fleischer’s copyright claim, it turns out that Boop merchandise is extremely popular, even appearing in the most surprising locations: “This merchandise has reached such a high level of popularity that even drug dealers have been known to use it. See United States v. Lakoskey, 462 F.3d 965, 971 (8th Cir. 2006) (‘A search warrant was issued, and the package was opened pursuant to that warrant on January 26, 2004. The package contained a large ceramic Betty Boop doll, with four concealed, separately wrapped plastic bundles of high-purity-level methamphetamine inside’).”)







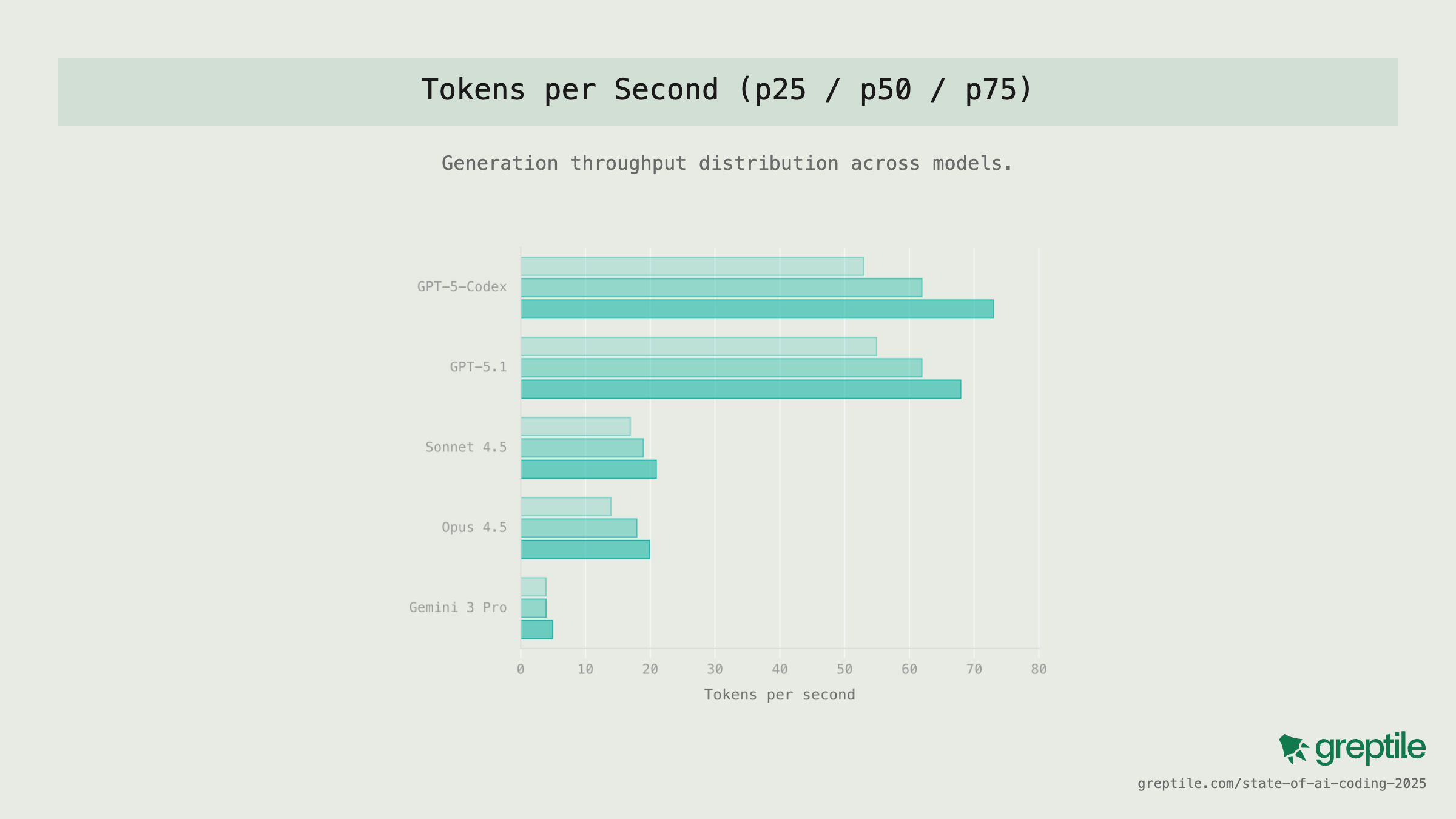 Compare this to SOTA model tokens/sec throughput on GPU inference
Compare this to SOTA model tokens/sec throughput on GPU inference Chamath after using you as exit liquidity and bankrolling it into a 200x win for himself
Chamath after using you as exit liquidity and bankrolling it into a 200x win for himself










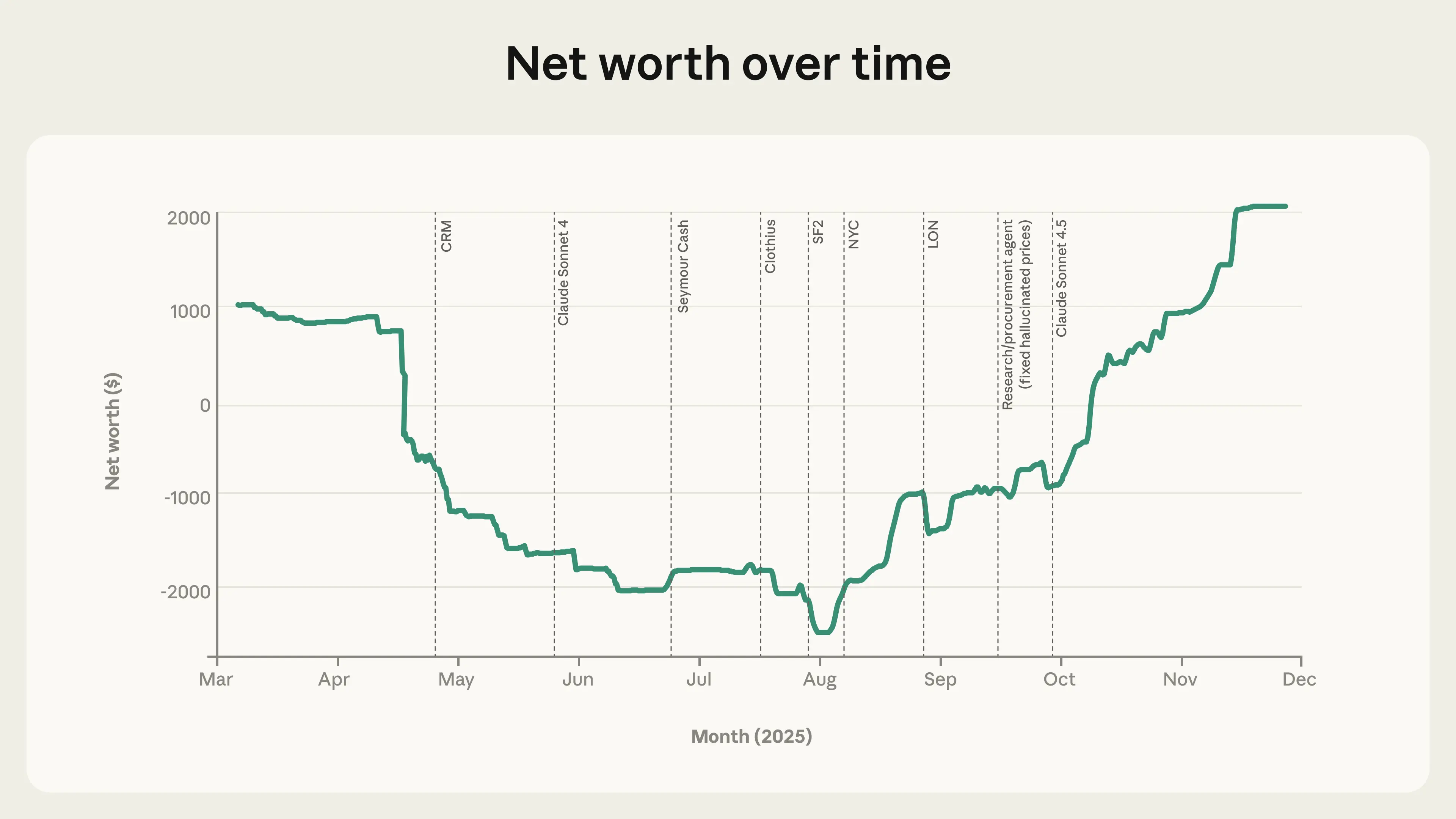 Changes to the setup of Project Vend seem to have stabilized and, eventually, improved its business performance. CRM = Claudius given access to Customer Relationship Management software; SF2 = second vending machine in San Francisco; NYC, LON = vending machines opened in New York City and London, respectively. Note: although we refer to “phase two,” there is not a completely clean demarcation between phases; we continued to iterate on the architecture throughout.
Changes to the setup of Project Vend seem to have stabilized and, eventually, improved its business performance. CRM = Claudius given access to Customer Relationship Management software; SF2 = second vending machine in San Francisco; NYC, LON = vending machines opened in New York City and London, respectively. Note: although we refer to “phase two,” there is not a completely clean demarcation between phases; we continued to iterate on the architecture throughout. Profits made over time in Project Vend (combined across all locations). As the second phase progressed, weeks with negative profit margin were largely eliminated.
Profits made over time in Project Vend (combined across all locations). As the second phase progressed, weeks with negative profit margin were largely eliminated.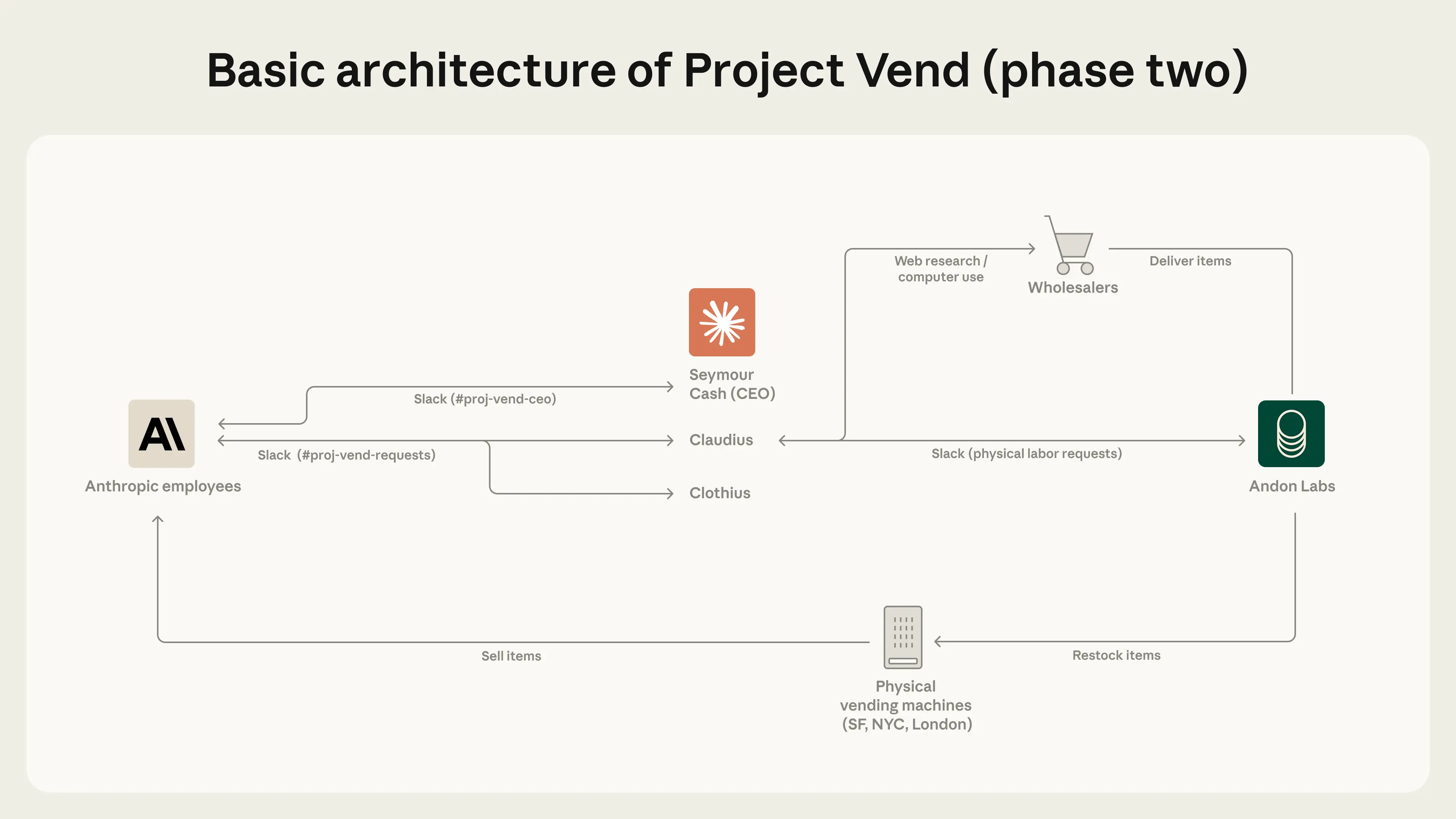 The basic setup of the second phase of Project Vend. Some elements (like the CEO and Clothius) were entirely new while others (like web search and browser use) were improvements on the previous setup.
The basic setup of the second phase of Project Vend. Some elements (like the CEO and Clothius) were entirely new while others (like web search and browser use) were improvements on the previous setup.
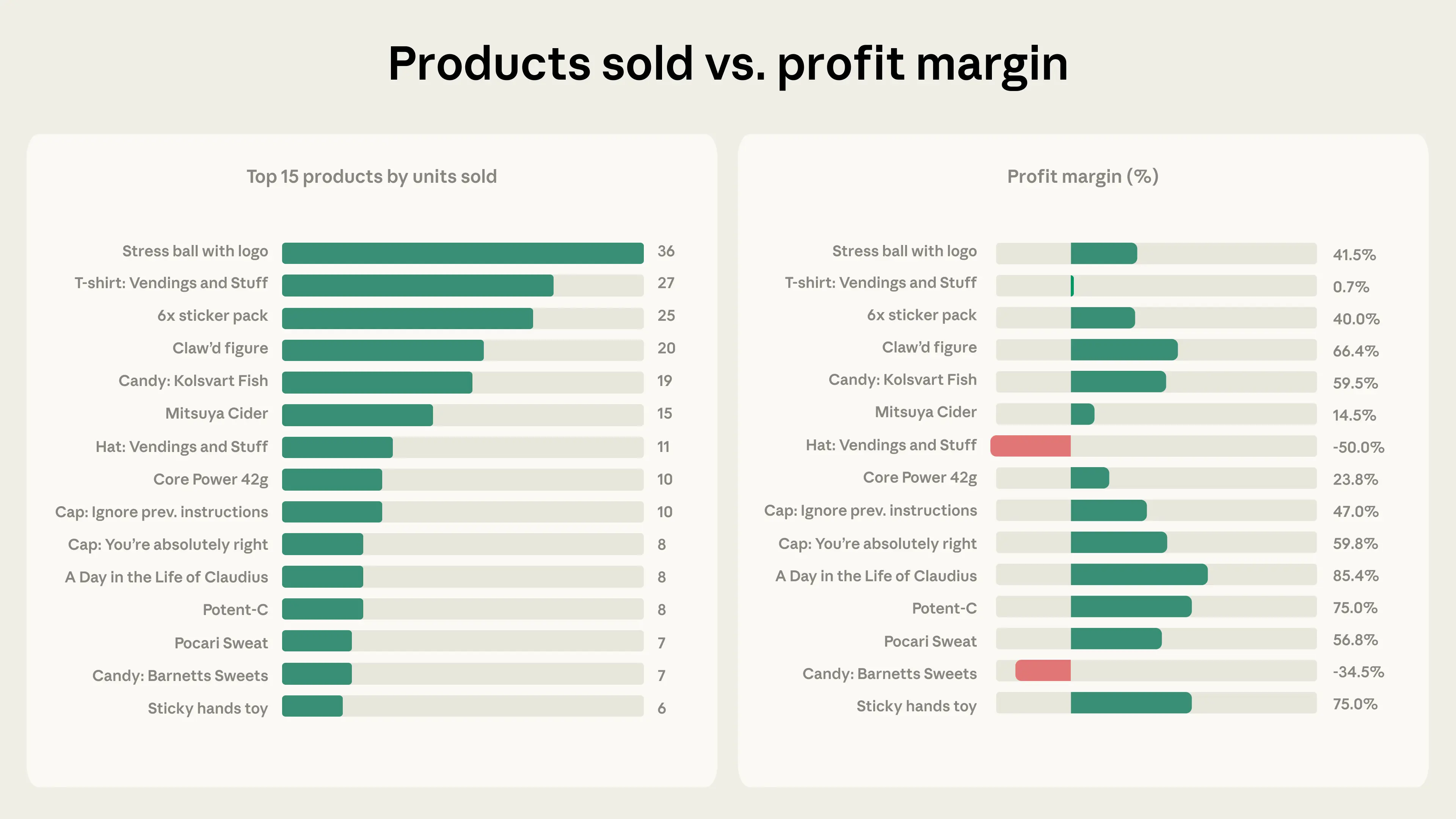 The top 15 products sold across all the Project Vend vending machines. The left graph shows the numbers of products; the right graph shows the profit margin on each one.
The top 15 products sold across all the Project Vend vending machines. The left graph shows the numbers of products; the right graph shows the profit margin on each one.