Securing Things on the Internet
WHAT WE DO
1
Licensed as an SDK/API to IoT device developers and OEMs, |pipe| creates an authenticated, encrypted path over the Internet (like a VPN) directly between the connected device and an authorised smartphone browser, without any intermediary server.
Licensed as an SDK/API to IoT device developers and OEMs, |pipe| creates an authenticated, encrypted path over the Internet (like a VPN) directly between the connected device and an authorised smartphone browser, without any intermediary server.
Securing Things on the Internet
HOW IT WORKS
2
Securing Things on the Internet
SECURE YET SIMPLE
3
-
carrying real-time data, audio and video plus proxied webpages
-
providing a simple user experience for claiming a new device
-
works on both local and remote IP networks (LAN/WAN)
-
leverages existing Web standards, including WebRTC
-
We license |pipe| as a security toolkit
(SDK/API) to IoT device developers & OEMs: device code, branding and tech support.
-
We charge a single royalty per device
shipped so you can easily calculate this per unit cost into your Bill of Materials.
-
You avoid paying recurrent (time-based) costs
for bandwidth and cloud server management after your device has shipped.
-
We license |pipe| as a security toolkit
(SDK/API) to IoT device developers & OEMs: device code, branding and tech support.
-
We charge a single royalty per device
shipped so you can easily calculate this per unit cost into your Bill of Materials.
-
You avoid paying recurrent (time-based) costs
for bandwidth and cloud server management after your device has shipped.
4
Securing Things on the Internet
YOU + YOUR THINGS
5
-
01
-
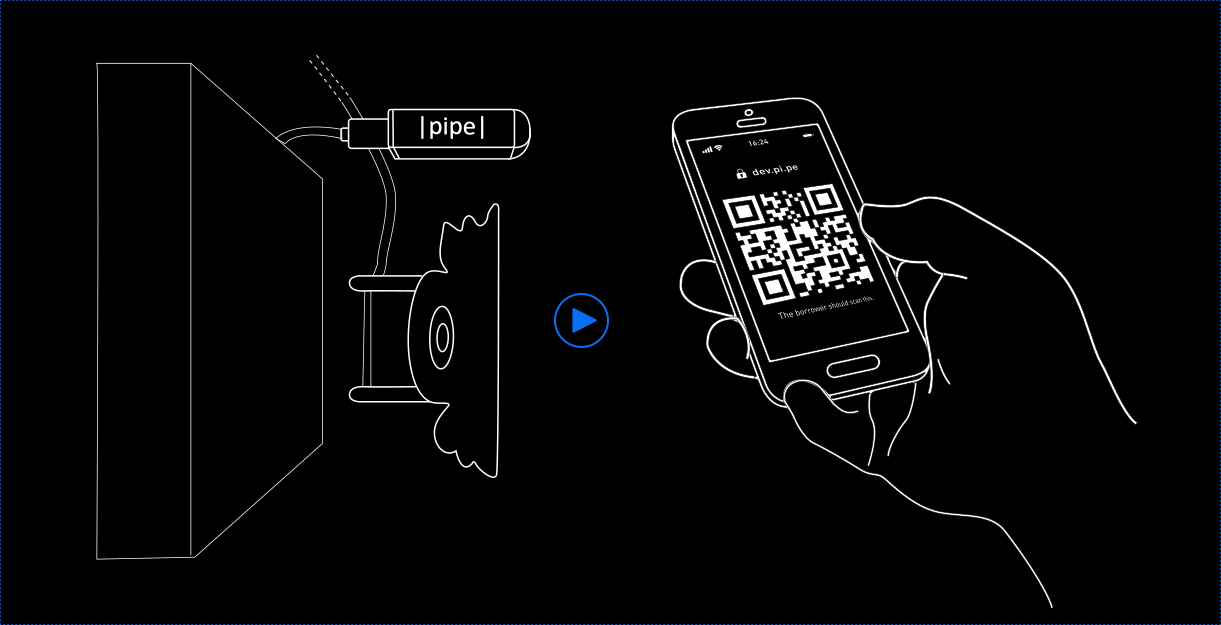
PAIRING AN IOT DEVICE
We call this Secure Proximity-Based Pairing. For example, just snap the QR code displayed by the new device with your smartphone camera.
-
02
-
cryptographic keys
Keys are exchanged directly between the smartphone and IoT device, creating a direct encrypted channel with no intermediary server nor certification authorities, so privacy is assured.
-
03
-
CONNECT DEVICES TOGETHER
You can lend your device to someone and assign them usage rights, or connect devices together. You own the device/s so you have control.
Simply secure and private - by design
Privacy Policy last revised: June 9th, 2021