Alice and Bob are the world’s most famous cryptographic couple. Since their invention in 1978, they have at once been called “inseparable,” and have been the subject of numerous divorces, travels, and torments. In the ensuing years, other characters have joined their cryptographic family. There’s Eve, the passive and submissive eavesdropper, Mallory the malicious attacker, and Trent, trusted by all, just to name a few.
While Alice, Bob, and their extended family were originally used to explain how public key cryptography works, they have since become widely used across other science and engineering domains. Their influence continues to grow outside of academia as well: Alice and Bob are now a part of geek lore, and subject to narratives and visual depictions that combine pedagogy with in-jokes, often reflecting of the sexist and heteronormative environments in which they were born and continue to be used. More than just the world’s most famous cryptographic couple, Alice and Bob have become an archetype of digital exchange, and a lens through which to view broader digital culture.
This website details the major events in the “lives” of Alice and Bob, from their birth in 1978 onwards. It is also the public, multimedia component for a related academic research project by Quinn DuPont and Alana Cattapan.
Synopsis
Alice and Bob are fictional characters originally invented to make research in cryptology easier to understand. In a now-famous paper (“A method for obtaining digital signatures and public-key cryptosystems”), authors Ron Rivest, Adi Shamir, and Leonard Adleman described exchanges between a sender and receiver of information as follows: “For our scenarios we suppose that A and B (also known as Alice and Bob) are two users of a public-key cryptosystem.” In that instant, Alice and Bob were born.
Read more...
Public-Key Cryptography Invented in Secret
 In the early 1970s, public key cryptography was invented in secret by the GCHQ. This is the technology that would later lead to the birth of Alice and Bob.
In the early 1970s, public key cryptography was invented in secret by the GCHQ. This is the technology that would later lead to the birth of Alice and Bob.
Read more
1970-1973
Public-Key Cryptography is Re-Invented
 In November 1976, Whitfield “Whit” Diffie and Martin Hellman published a paper entitled “New Directions in Cryptography” in IEEE Transactions in Information Theory. The paper demonstrated that it was possible to securely exchange information over non-secure channels, which they called public key cryptography.
In November 1976, Whitfield “Whit” Diffie and Martin Hellman published a paper entitled “New Directions in Cryptography” in IEEE Transactions in Information Theory. The paper demonstrated that it was possible to securely exchange information over non-secure channels, which they called public key cryptography.
Read more
November, 1976
RSA Algorithm Developed
Diffie and Hellman’s proposal for public key cryptography set the course for future research, but their analysis still lacked the all-important one-way function,  needed to generate the public and private key parts. Moreover, there was no working implementation of the cryptosystem. In 1977, young MIT computer scientists Ronald Rivest, Adi Shamir, and Leonard Adleman found a suitable one-way function and then developed a working implementation of public key cryptography.
needed to generate the public and private key parts. Moreover, there was no working implementation of the cryptosystem. In 1977, young MIT computer scientists Ronald Rivest, Adi Shamir, and Leonard Adleman found a suitable one-way function and then developed a working implementation of public key cryptography.
Read more
1977-78
RSA Algorithm Publicized in Scientific American
As soon as Ron Rivest, Adi Shamir, and Leonard Adleman discovered what they believed to be a suitable one-way function for their version of public key cryptography, Rivest sent a copy of the draft paper outlining their cryptosystem to Martin Gardner, a mathematics columnist at Scientific American. The subsequent publication popularized the RSA algorithm and brought it under scrutiny.
Read more
August, 1977
Alice and Bob are Born
 Five years after public key cryptography was invented at GCHQ, two years after public key cryptography was re-invented by Diffie and Hellman, and a year and two articles after a practical cryptosystem was developed by Ron Rivest, Adi Shamir, and Leonard Adleman, Alice and Bob are finally born.
Five years after public key cryptography was invented at GCHQ, two years after public key cryptography was re-invented by Diffie and Hellman, and a year and two articles after a practical cryptosystem was developed by Ron Rivest, Adi Shamir, and Leonard Adleman, Alice and Bob are finally born.
Read more
February, 1978
RSA Data Security Founded
 Ron Rivest, Adi Shamir, and Leonard Adleman realized that their public key cryptography algorithm was commercially valuable, and in December 1978 they filed for a patent (through MIT) and began assembling a commercial enterprise, RSA Data Security.
Ron Rivest, Adi Shamir, and Leonard Adleman realized that their public key cryptography algorithm was commercially valuable, and in December 1978 they filed for a patent (through MIT) and began assembling a commercial enterprise, RSA Data Security.
Read more
1982
Alice and Bob Become Tropes of Cryptology Research
After their birth in 1978, Alice and Bob soon became tropes of cryptology research. Over the next decade of academic research in cryptology, Alice and Bob would become ubiquitous and a key epistemic tool.

Image of Alice and Bob by Shamir, Rivest, and Adleman
Read more
1980-
Alice and Bob After Dinner Speech
In 1984, a year after Ron Rivest, Adi Shamir, and Leonard Adleman received the patent for the RSA algorithm—and still early days for Alice and Bob—the cryptologist John Gordon gave an “after-dinner speech” about Alice and Bob at an April conference in Zurich.
Read more
April, 1984
Alice and Bob Move
While Alice and Bob were born in the academic field of cryptology, they were soon being used in many other disciplines, domains, and contexts.
Read more
1980-
Eve is Born
As was customary for cryptology literature by this point, Charles Bennett, Gilles Brassard, and Jean-Marc Roberts opened their 1985 abstract “How to Reduce Your Enemy’s Information” with a story about Alice and Bob. This time, however, a new character was introduced: Eve.
Read more
1985-88
The Culture of Alice and Bob
As Alice and Bob became common features of the academic landscape, and as the 1990s and 2000s saw a rise of nerd and geek culture, Alice and Bob were soon found across digital culture broadly. Their depiction in popular media is usually a winking subcultural reference, signaling awareness of geek lore.

The popular (and often user-generated) ecard website someecards includes a card that portrays Bob passing a note Eve, with Alice none the wiser.

In 2008, Physics World readers voted this cover one of their favourite covers of all time.
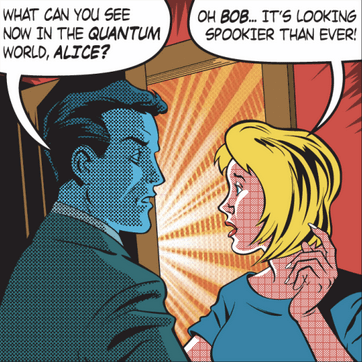
An image for the cover of Physics World from March 2013. A letter to the editor was published in the April 2013 issue critiquing the gendered stereotypes in this image.
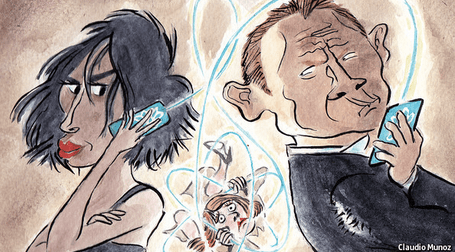
An image depicting Alice, Bob, and Eve from a 2013 article in the Economist on quantum-secured data.

A T-shirt referencing some of the key figures in the "dramatis personae" of characters.
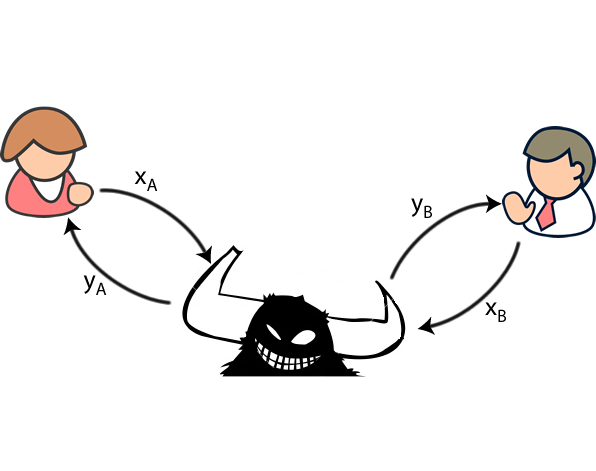
Image of Alice, Bob, and Eve (here depicted as a horned monster), from the cryptography and physics teaching website of Alastair Kay.
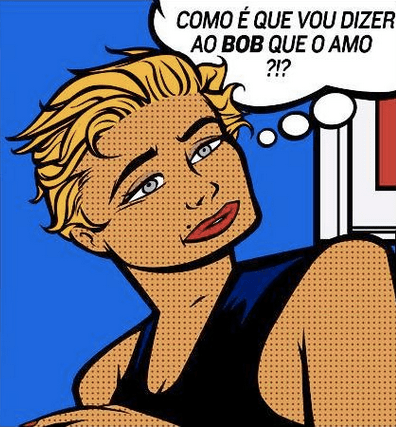
A depiction of Alice in Portuguese. Alice asks, "How am I going to tell Bob I love him?"
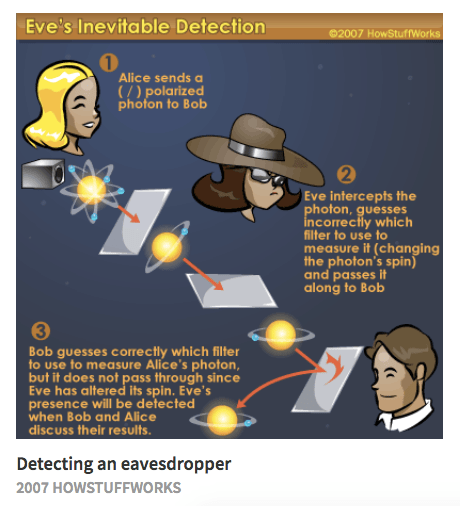
A diagram from 2007 demonstrating interception in quantum cryptology, with Alice, Bob, and Eve.
Detail from painting by Molly Crabapple, entitled "Alice, Bob, and Eve".
Read more
1990-
The “Adventures of Alice and Bob”
 In 2011, RSA Security LLC made Alice and Bob the theme for their annual security industry conference.
In 2011, RSA Security LLC made Alice and Bob the theme for their annual security industry conference.
Read more
2011
Cultural Interpretations of Alice and Bob
In 2012, the computer scientist Srini Parthasarathy wrote a document entitled “Alice and Bob can go on a holiday!”.  Rearticulting the deeper culture in which Alice and Bob lived, Parthasarathy proposed that Alice and Bob might be usefully replaced by Sita and Rama, characters central to Hindu mythology.
Rearticulting the deeper culture in which Alice and Bob lived, Parthasarathy proposed that Alice and Bob might be usefully replaced by Sita and Rama, characters central to Hindu mythology.
Read more
2012
On Gender
In the history of cryptology, women tend to be either systematically excluded or reduced to objects. The absence of women is both a reflection of the bias of society and historians, and a gap in the employment of women in computing fields. In the early history of computing, in fact, women were key to the development of computing, and especially cryptology (see Woodfield, 2001; Misa (ed.), 2010; Hicks, 2017). But, once computing gained status and importance, women were increasingly pushed out of the computer and cybersecurity industry. Worrisomely, in the field of cybersecurity, this trend to marginalize and exclude women has increased in recent years. Those women that have managed to elbow in on the male-dominated industry are important to highlight and celebrate. Uncovering the gendered context of Alice and Bob is one chapter in the larger, untold story of women in cryptology.
Read more...Download Full Text
Download full-text (PDF) for offline reading (6200 words; 30 minutes reading time).
Contact
Research by Quinn DuPont and Alana Cattapan. DuPont developed the website, and received institutional and financial support through a Rutgers Digital Studies Fellowship and UVic Electonic Textual Cultures Lab Open Knowledge Practicum. Corrections, suggestions, and responses warmly welcomed: